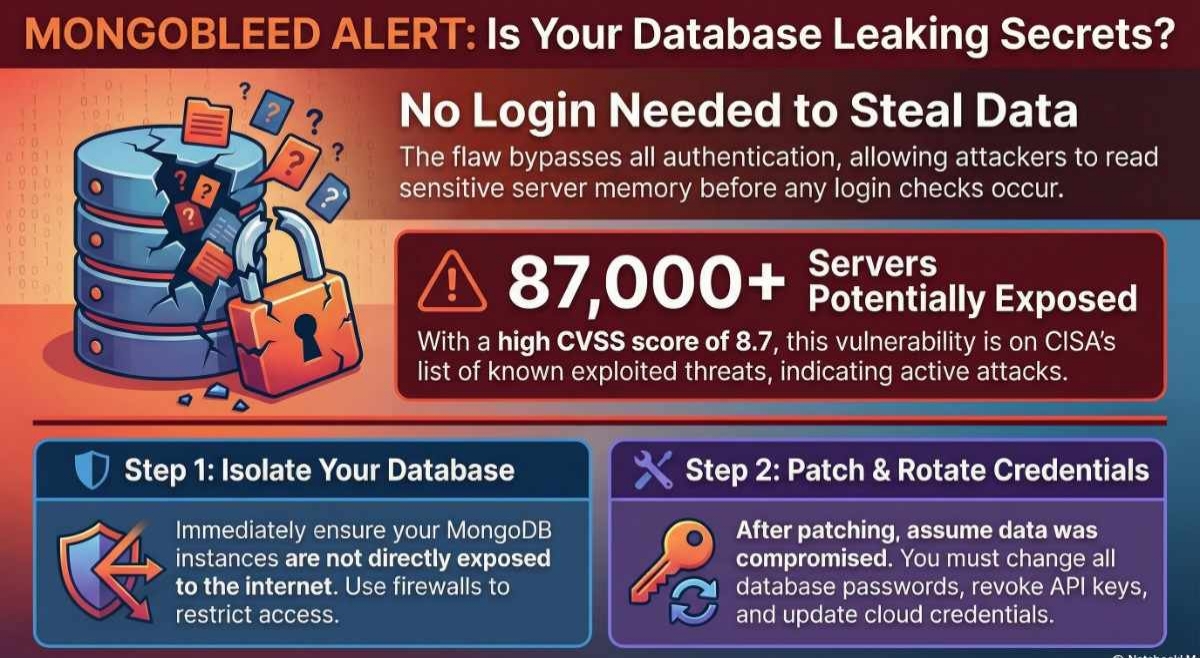
Late December 2025 brought a serious wake-up call for anyone running MongoDB databases. The vulnerability, known as Mongobleed Vulnerability (CVE-2025-14847), hit the headlines fast because attackers can pull sensitive data straight from your server’s memory without even logging in.
Most database problems need some kind of access first, but this one doesn’t. It strikes right away, before any checks happen. That’s what makes it so risky for businesses like yours.
It carries a high CVSS score of 8.7, and scans show over 87,000 MongoDB instances could be exposed online. In early 2026, this quickly became one of the top database threats to watch.
Things got more urgent when CISA added it to their Known Exploited Vulnerabilities list on December 29, 2025. That means real attacks are happening, and federal agencies have until January 19, 2026, to fix it.
What Is the Mongobleed Vulnerability (CVE-2025-14847)?
At its core, Mongobleed Vulnerability is a flaw that lets unauthorized users grab bits of memory from MongoDB servers. It happens because of how the system deals with inconsistencies in compressed data packets using zlib.
When the server gets a tricky, compressed message, it can end up allocating extra memory and sending back parts that haven’t been cleared out. Since this all occurs before any login, no credentials are needed to pull it off.
In short, if your MongoDB setup is reachable over the network and has zlib compression turned on, it’s open to this attack.
Why Mongobleed Vulnerability Is Extremely Dangerous
No Authentication Required
Flaws like this, that hit before any login, are always the toughest to defend against. Things like strong passwords or multi-factor authentication won’t help here because the exploit bypasses them completely.
If your database port is open to the internet with compression enabled, you’re vulnerable right now.
Potential for Serious Data Leaks
Those leaked memory chunks might include all sorts of critical info, such as:
- Database login details
- API keys and tokens
- Cloud service credentials
- User session information
- Personal customer data
MongoDB often holds your company’s most important records and secrets, so even small leaks could lead to big problems down the line.
Quick Spread Among Attackers
A proof-of-concept exploit went public on December 26, 2025, just days after disclosure. That made it easy for all kinds of threats—from script kiddies to pros—to jump in fast.
Why It Reminds Us of Heartbleed
Experts can’t help comparing Mongobleed to the notorious Heartbleed bug. Both let attackers peek at uncleared memory, and it’s tough to know exactly what got exposed.
The key difference? Heartbleed hit web encryption, while this one goes straight for your databases, risking credentials and private data immediately.
Which MongoDB Versions Are Impacted
This affects a wide swath of releases:
- Vulnerable ranges: Versions 4.4 up to 8.2
- Older ones without fixes: 3.6, 4.0, and 4.2 remain exposed forever
If you’re on those end-of-life versions, you’ll stay at risk until you upgrade to something supported.
Encryption Won’t Save You Here
A common misconception is that TLS protects against everything. But with Mongobleed, it doesn’t. Encryption secures data on the wire, yet the flaw kicks in after decryption, inside the database process itself.
So, even fully encrypted connections leave you open.
Key Takeaways From This Mongobleed Event
Pre-Auth Issues Top the Danger List
When attackers don’t need credentials, your usual defenses fall short. This case shows why you must prioritize any flaw that allows access before authentication.
Lock Down Network Access
Many breaches could have been avoided with better segmentation. Never leave MongoDB directly facing the internet.
Instead, try these steps:
- Limit port 27017 to only your trusted apps and servers
- Use firewalls and private network controls
- Cut off any unneeded external access
Patching Isn’t the Whole Story
Since memory leaks hide what was taken, you can’t just patch and forget. Assume some data might already be out there.
Right after updating:
- Change all database passwords
- Revoke and replace API keys
- Update cloud credentials
- Clear out sessions and tokens
Better safe than sorry—treat it as potentially compromised.
Signs of Possible Exploitation
Watch for these red flags in your monitoring:
- Spikes in connections, even over 100,000 per minute
- Unexpected jumps in CPU or memory use
- Big data responses to unknown clients
Dig into logs for unusual patterns around connections and resource spikes.
Short-Term Fix: Turn Off zlib Compression
If you can’t patch right away, disable zlib as a workaround. Switch to options like snappy or zstd instead.
It closes the door on this exploit path, though you might notice a bit more bandwidth usage.
Broader Lessons for Managing Vulnerabilities
Mongobleed’s fast timeline—from reveal to real attacks in days—highlights today’s threat speed.
You need solid visibility, like:
- Full inventory of all your databases, even overlooked ones
- Quick ways to spot shadow or old setups
- Plans for emergency updates on hot exploits
Legacy versions pose the biggest ongoing threat, so plan migrations soon.
Key Takeaways
- Don’t expose databases publicly—segment networks tightly.
- Patch fast, but follow up with credential rotations.
- Monitor for odd connection behavior.
- Disable risky features like zlib if needed temporarily.
- Keep assets inventoried and up to date.
Final Thoughts
The Mongobleed vulnerability (CVE-2025-14847) drives home that strong database security goes beyond logins and encryption. Open exposures, slow fixes, and pre-auth flaws can turn trusted tools into liabilities overnight.
Stay ahead with isolation, watching closely, quick action, and good maintenance. This incident shows mature platforms aren’t immune, and fast response separates minor scares from major breaches.

