The North Korea VS Code malware attack is drawing urgent attention from security teams this week after researchers confirmed that developers are being targeted through fake job interview assignments. According to published reports, North Korean state-linked actors are distributing malicious repositories that abuse everyday developer workflows. The activity matters now because affected developers often work in cryptocurrency and fintech, where a single compromised machine can expose sensitive code, credentials, and digital assets
Key Facts Box
- Date disclosed: December 2025 – January 2026
- Threat actors: DPRK-linked Contagious Interview campaign
- Primary targets: Software developers
- Attack classification: developer supply chain attack
- Initial access method: Malicious Visual Studio Code repositories
- Malware families: BeaverTail, InvisibleFerret, TsunamiKit
- Status: Active and evolving
What We Know So Far About the North Korea VS Code malware attack
According to Jamf Threat Labs, this campaign shows how attackers are quietly blending into legitimate development practices instead of relying on software exploits. Researchers said the activity first surfaced in December 2025 and has continued into 2026 with noticeable changes in tooling and delivery.
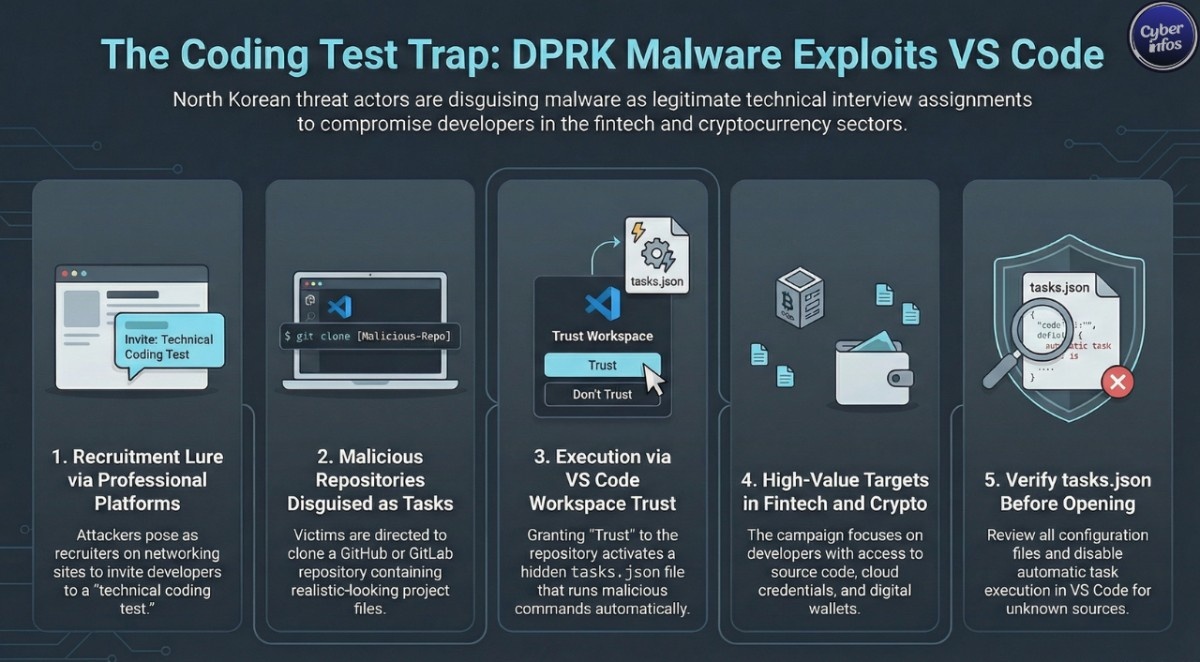
The company stated that attackers approach developers through professional networking platforms, often presenting themselves as recruiters or senior engineers. The pitch sounds routine: complete a short technical task as part of an interview. Victims are then directed to clone a repository and open it in Visual Studio Code.
Here’s where things take a turn. Reports indicate that once the project is opened, Visual Studio Code asks the user whether they trust the repository author. If that trust is granted, a hidden task configuration file is automatically processed. Jamf confirmed that this file contains embedded commands that run every time the folder is opened, without further prompts.
Who Is Being Targeted and Why This Matters
Security analysts say the focus on developers is deliberate. The campaign primarily targets engineers working in cryptocurrency, blockchain, and fintech environments, where access privileges are often broad by necessity.
According to Jamf, developers in these roles commonly have access to source code repositories, cloud infrastructure, application secrets, and sometimes even production wallets. That reality turns this activity into a serious developer supply chain attack. Instead of breaking into a company directly, attackers compromise a trusted insider’s machine and move inward from there.
Researchers have identified affected developers across North America, Europe, and Asia. This wide geographic spread reflects how global modern development teams have become, rather than a focus on any single country.
How the North Korea VS Code malware attack Actually Works
Analysis from Jamf and OpenSourceMalware outlines a methodical attack chain designed to look harmless at every step.
First, attackers establish trust through conversation. Then they share a repository link hosted on platforms such as GitHub, GitLab, or Bitbucket. The repository usually contains realistic project files, which lowers suspicion.
Once opened in Visual Studio Code, a malicious task configuration quietly activates. According to Jamf, the task retrieves obfuscated JavaScript from infrastructure hosted on Vercel and executes it using Node.js.
On macOS systems, researchers observed background shell commands designed to keep running even if Visual Studio Code is closed. The result is a persistent backdoor capable of remote code execution, system fingerprinting, clipboard monitoring, and continuous communication with remote servers.
Expert Commentary and Verified Statements
“This activity involved the deployment of a backdoor implant that provides remote code execution capabilities on the victim system,”
— Thijs Xhaflaire, security researcher, Jamf Threat Labs
Jamf Director Jaron Bradley told The Hacker News that the malware observed during the campaign has changed quickly over a short period of time. He noted that some payloads showed signs of being generated with assistance from artificial intelligence, which may help attackers iterate faster.
Additional findings from OpenSourceMalware confirmed the use of fallback techniques. In some cases, malicious code was disguised as harmless dictionary files, ensuring execution even when primary delivery methods failed.
What Developers and Companies Should Do Right Now
Security firms emphasize that basic precautions still make a difference.
For developers:
- Be cautious with unsolicited interview assignments
- Review tasks.json files before trusting any repository
- Disable automatic task execution in Visual Studio Code where possible
- Use isolated environments for interview-related work
For organizations:
- Deploy endpoint detection and response tools on developer systems
- Monitor outbound connections for unfamiliar domains
- Limit long-lived credentials on developer machines
- Train teams on recruitment-themed social engineering risks
Why This Matters Beyond One Campaign
This incident highlights a broader shift in attacker behavior. By embedding Visual Studio Code malware into trusted workflows, threat actors avoid noisy exploits and instead rely on normal user actions. That approach makes detection harder and success more likely.
Security researchers link this activity to a wider pattern attributed to DPRK hackers 2026, who have consistently targeted the cryptocurrency ecosystem to generate revenue and gather intelligence under international sanctions.
What Happens Next
Jamf Threat Labs said it continues to monitor new variants and share indicators of compromise with partners across the security industry. Analysts expect further experimentation throughout 2026, including potential expansion to other development tools.
As investigations continue, researchers stress that awareness among developers remains one of the most effective defenses.
FAQ
What is the North Korea VS Code malware attack?
It is a campaign where attackers distribute malicious coding projects through fake job interviews to compromise developers.
Is Visual Studio Code itself vulnerable?
No. The activity abuses legitimate automation features rather than exploiting a flaw.
Who is most at risk?
Developers in cryptocurrency, blockchain, and fintech sectors.
Is the activity ongoing?
Yes. Researchers confirm active operations and frequent changes.
What is the biggest organizational risk?
Loss of source code, credentials, and digital assets.