The cybersecurity community is closely watching developments around the WIRED data breach, after threat actors claimed responsibility for leaking a massive dataset tied to the publication’s subscriber base. According to multiple security researchers, more than 2.3 million subscriber records linked to WIRED, one of the most influential technology media brands under the Condé Nast umbrella, were allegedly exposed on underground forums during the Christmas period.
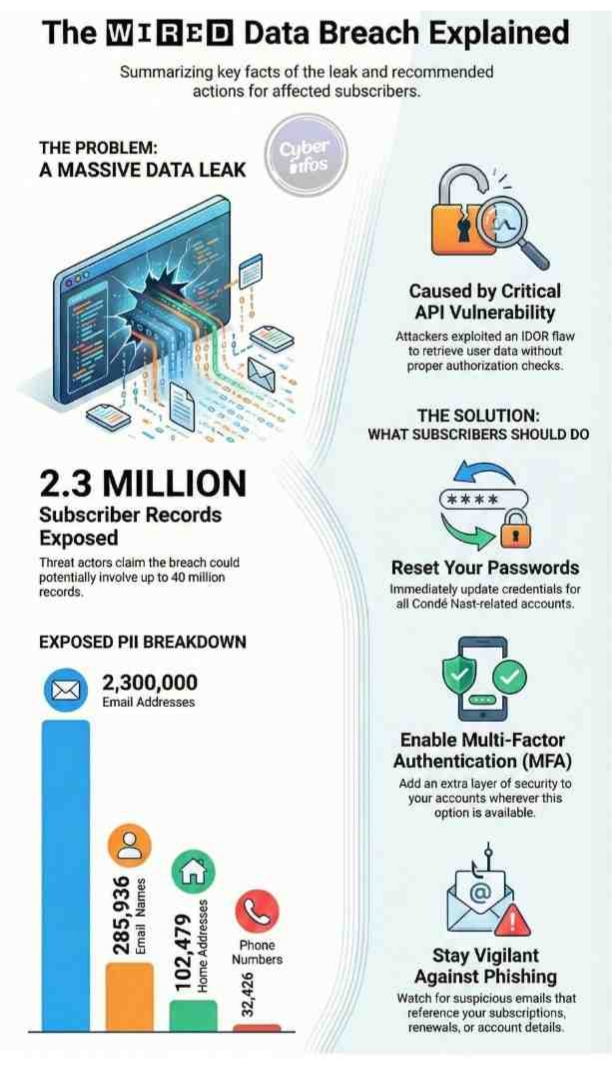
The breach surfaced publicly when a threat actor using the alias “Lovely” began advertising access to the dataset on cybercrime marketplaces. What initially appeared to be a limited leak has since escalated into a potentially wider exposure, with claims that as many as 40 million records from Condé Nast’s broader ecosystem could be involved. If confirmed, the WIRED data breach would represent one of the most significant media-sector data exposures in recent years.
What Subscriber Data Was Exposed
Early analysis suggests the WIRED data breach involved extensive personally identifiable information (PII), although no direct financial data such as credit card numbers has been confirmed so far. The exposed dataset reportedly contains:
| Data Type | Approximate Count |
|---|---|
| Email addresses | 2,300,000 |
| Names | 285,936 |
| Home addresses | 102,479 |
| Phone numbers | 32,426 |
Security analysts reviewing the leaked samples noted that the data appears in structured JSON-based subscriber profiles, including internal user IDs, account creation timestamps dating back to 2011, and activity records extending into late 2025. While the absence of passwords may reduce immediate financial risk, the exposed information is more than sufficient to enable phishing, impersonation, and identity-based social engineering attacks.
How the WIRED Data Breach Allegedly Occurred
Technical findings shared by independent researchers suggest the breach stemmed from Insecure Direct Object Reference (IDOR) vulnerabilities within Condé Nast’s subscription infrastructure. By manipulating user identifiers, attackers were allegedly able to retrieve subscriber data without proper authentication or authorization checks.
Further analysis indicates weaknesses in access control mechanisms tied to account management endpoints. These flaws may have allowed attackers to query user profiles at scale while remaining largely invisible to traditional security monitoring tools. In the context of the WIRED data breach, this highlights a broader industry challenge: API-level vulnerabilities often bypass perimeter defenses and remain undetected until significant damage has occurred.
Threat Actor “Lovely” and Disclosure Claims
The individual or group operating under the alias “Lovely” claims responsibility for the breach and has been active across underground forums. According to their statements, they attempted to disclose the vulnerabilities responsibly prior to publication. The actor alleges that outreach was made to Condé Nast and security intermediaries, including outreach via DataBreaches.net, but received no meaningful response.
Following what they describe as ignored warnings, the attacker proceeded to release portions of the dataset publicly. They further claimed the absence of a published security.txt file hindered responsible reporting. As of this writing, Condé Nast has not released a detailed public response addressing these specific claims.
Independent Verification and Research Findings
Independent cybersecurity firm Hudson Rock analyzed portions of the leaked data and found strong correlations between the exposed email addresses and credentials previously harvested by malware families such as RedLine and Raccoon. This overlap reinforces the likelihood that the data is authentic and already circulating within criminal ecosystems.
In addition, breach monitoring service Have I Been Pwned has indexed the dataset, confirming that affected individuals are now receiving exposure notifications. These independent validations add significant credibility to the claims surrounding the WIRED data breach.
Potential Impact Across Condé Nast Brands
A major concern arising from the incident is the possibility that the breach extends beyond WIRED itself. According to the attacker, the compromised systems may underpin a shared identity framework used across multiple Condé Nast properties, including titles such as Vogue and The New Yorker.
If accurate, this would dramatically increase the scope of the incident, placing millions more subscribers at potential risk. Even without direct financial data, exposed contact details can be leveraged for phishing, account takeover attempts, and highly targeted social engineering campaigns.
What Affected Subscribers Should Do
Individuals who believe they may be impacted by the WIRED data breach should take immediate precautionary steps:
- Reset passwords for all Condé Nast-related accounts
- Avoid reusing credentials across services
- Enable multi-factor authentication wherever available
- Remain vigilant for phishing emails referencing subscriptions or renewals
- Monitor credit activity if physical address data was exposed
Broader Implications for Media Organizations
The WIRED data breach serves as a powerful reminder that media companies, despite not being traditional financial institutions, hold vast amounts of sensitive user data. Centralized subscription systems create efficiency—but also concentrate risk.
As digital publishers continue to scale, robust access controls, continuous security testing, and transparent vulnerability disclosure processes are no longer optional. In an era where trust underpins audience loyalty, cybersecurity resilience has become inseparable from journalistic credibility.
Final thoughts
The WIRED data breach is a clear reminder that no platform is immune to cyber risk. When millions of personal records are exposed, the impact goes far beyond headlines, it affects real people, real trust, and real security. Now is the time to take action.
If you’re a subscriber, update your passwords, enable multi-factor authentication, and stay alert for suspicious activity. If you’re an organization, treat this as a wake-up call to audit systems, fix access gaps, and prioritize user protection. Cybersecurity isn’t optional anymore, it’s a responsibility.
Stay informed, stay proactive, and don’t wait for a breach to act.

