Cybersecurity weekly report: This weekly cybersecurity roundup makes one thing clear right away 2026 did not start quietly. Instead of flashy, highly technical attacks, many threat actors leaned into trust abuse, third-party exposure, and identity compromise. According to multiple intelligence providers, a claimed NordVPN development-environment exposure, a confirmed Global-e incident affecting Ledger customers, and Russia-aligned activity abusing consumer messaging apps set the tone for the week. At the same time, ransomware attacks January 2026 continued at a familiar pace, reinforcing patterns already visible across recent data breach news 2026 and the latest threat intelligence report releases.
Weekly cybersecurity roundup: what mattered most this week
This weekly cybersecurity roundup feels less like a break from 2025 and more like a direct continuation. Analysts consistently pointed out that attackers are no longer relying on novelty alone. Instead, they are exploiting predictable gaps—trusted vendors, exposed credentials, and platforms that security teams still struggle to monitor closely.
Ransomware remained steady, vulnerabilities kept surfacing, and defenders were already balancing multiple security vulnerabilities patches while planning for January updates. In short, there was no easing into the year.
Major incidents in this cybersecurity weekly report
NordVPN development-environment exposure claim
On 4 January, a threat actor known as “1011” claimed on BreachForums to have accessed a NordVPN-related server and exfiltrated several databases. Screenshots allegedly showing Salesforce API keys and Jira tokens spread quickly, driving early data breach news 2026 coverage and customer anxiety.
NordVPN responded by explaining that the system was a third-party development and testing environment used during vendor evaluation. According to the company, it contained only synthetic data and remained isolated from production systems and real customer information. As of 6 January, analysts reported no credible evidence disputing this explanation.
Even without confirmed customer impact, the episode shows how development environments can become focal points in supply chain cyber attacks, largely because perception travels faster than technical verification.
Global-e and Ledger supply-chain exposure
Global-e disclosed unusual activity in its cloud infrastructure and later confirmed unauthorized access to customer data connected to Ledger orders. Ledger followed up by confirming that names and contact details were exposed and warned customers to remain alert for phishing attempts.
Researchers noted claims from data broker ShinyHunters suggesting a broader dataset may have been accessed, though this figure remains unverified. Regardless of scope, analysts described the incident as a textbook example of supply chain cyber attacks, where a single provider’s issue creates ripple effects across multiple brands.
For defenders, this type of exposure increasingly shapes incident response cybersecurity planning, particularly around notification timing and third-party visibility.
Russia-aligned malware campaign via Viber
A detailed malware campaign analysis this week highlighted activity by Russia-aligned actor UAC-0184. The group targeted Ukrainian government and military organizations by abusing the Viber messaging app—an approach designed to bypass traditional email defenses.
Messages delivered malicious ZIP files containing LNK shortcuts. Once opened, these files triggered PowerShell scripts, DLL side-loading, and deployment of Hijack Loader followed by Remcos RAT. Analysts emphasized that campaigns like this blur the line between consumer and enterprise risk, especially when credential theft attacks are part of the intrusion chain.
Credential theft as a primary entry point
Hudson Rock’s January analysis reinforced a trend that keeps resurfacing in data breach news 2026: many compromises begin with old, unrotated credentials rather than fresh zero-day exploits. According to researchers, attackers regularly recycle infostealer data to gain initial access, often without triggering immediate alarms.
This reality keeps identity hygiene at the center of incident response cybersecurity, especially for organizations that still rely on perimeter-centric defenses.
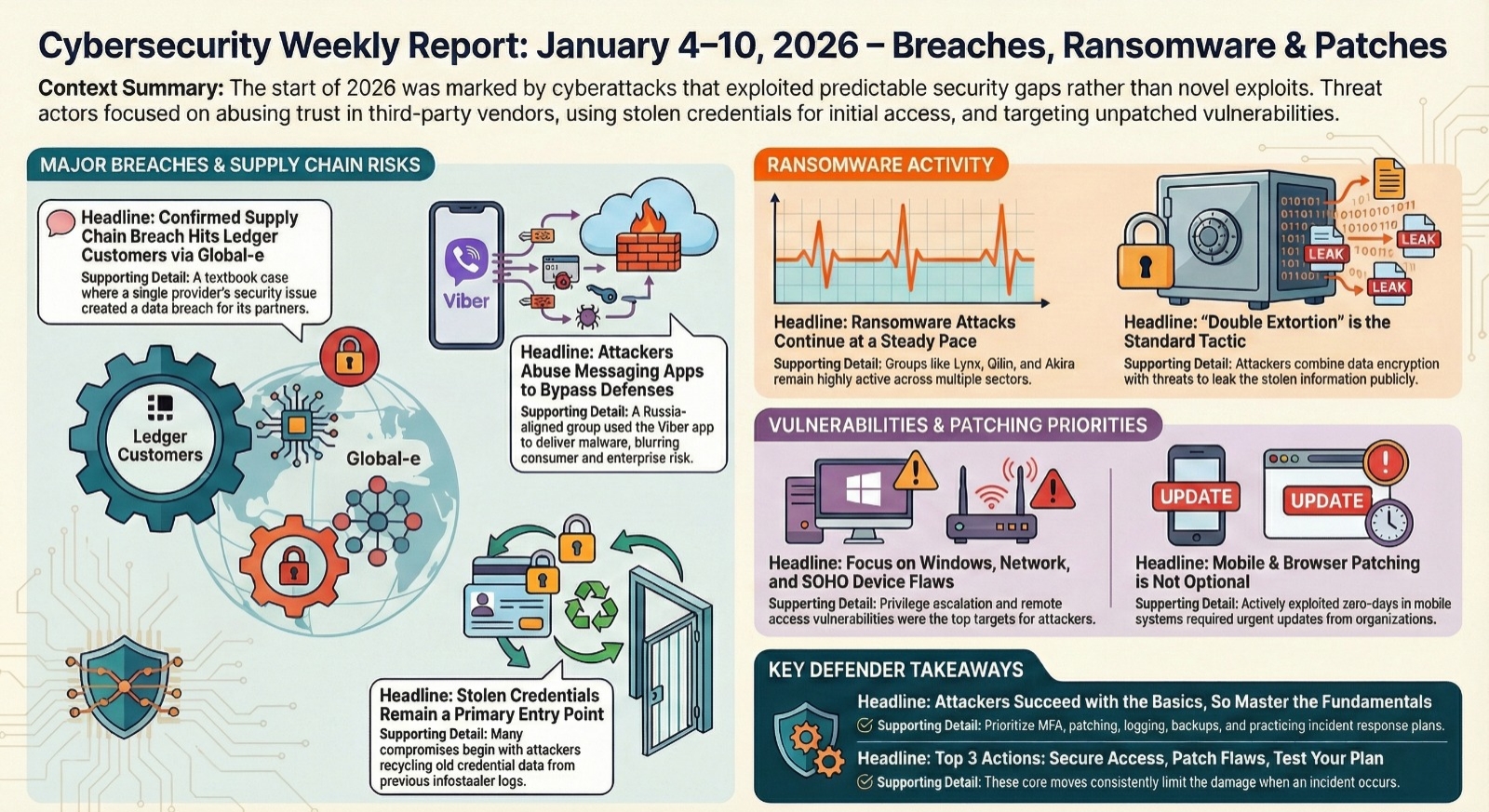
Security vulnerabilities patches and update activity
CVEs drawing attention
Early January vulnerability chatter focused on Windows privilege-escalation flaws and weaknesses in networking and SOHO devices. CVE-2025-50708 drew attention for its post-exploitation value, while edge-device flaws highlighted ongoing exposure outside traditional data centers.
These findings reinforce the importance of timely security vulnerabilities patches, particularly for systems that attackers can reach remotely.
Patch Tuesday outlook
January forecasts suggested a lighter Patch Tuesday, but analysts cautioned against complacency. Even smaller update cycles can introduce fixes for server-side or Internet-facing components that attackers move quickly to probe.
Preparation, testing, and prioritization remain the practical focus for most teams.
Mobile and browser updates
The Android January bulletin covered vulnerabilities across core components, while Apple’s December WebKit fixes for actively exploited zero-day exploits remained urgent for organizations that delayed updates over the holidays. Analysts again stressed that mobile patching must be treated as part of baseline security, not optional hygiene.
Ransomware attacks January 2026
Lynx and INC activity
Threat-intelligence reporting continued to follow Lynx, believed to be linked to the INC ransomware family. Recent incidents reflected classic double extortion ransomware tactics, pairing data theft with encryption and leak threats.
Victims spanned multiple sectors, reinforcing that ransomware operators remain opportunistic rather than industry-specific.
Qilin, Akira, and others
Monitoring data showed continued activity from Qilin, Akira, and Clop. Analysts described Qilin as particularly adaptable across platforms, while Akira maintained pressure on mid-market organizations.
These ransomware attacks January 2026 underline why ransomware remains one of the most disruptive threats facing enterprises.
What this cybersecurity weekly report tells defenders
This cybersecurity weekly report reinforces a familiar but uncomfortable truth. Attackers do not need exotic tooling to succeed. Identity abuse, third-party compromise, and delayed patching continue to open doors. Whether through credential theft attacks, unaddressed vulnerabilities, or trusted vendors, the same themes repeat.
Recent threat intelligence report findings show that organizations investing in fundamentals patching, MFA, logging, backups, and practiced incident response cybersecurity consistently limit damage when incidents occur.
Looking ahead
The next week will revolve around Patch Tuesday releases and early exploitation attempts. Analysts will also continue monitoring espionage campaigns abusing consumer platforms and the sustained pace of ransomware attacks January 2026.
For security leaders, the priorities remain practical and immediate: close known gaps, watch for credential reuse, and ensure response plans work under pressure. Longer term, reducing exposure from supply chain cyber attacks and strengthening identity controls remain key themes as 2026 unfolds.
Final Thoughts
This week’s roundup shows how 2026 is starting with stealthy but high‑impact risks: supply‑chain exposures, dev‑environment leaks, and relentless double‑extortion ransomware.
Instead of chasing every headline, focus on three foundations: harden identity (MFA everywhere, watch for infostealer‑exposed credentials), close obvious gaps (patch browsers, mobile OS, and Internet‑facing services), and pressure‑test your incident‑response and ransomware playbooks.
For CyberInfos readers, the next best step is simple: pick one weakness highlighted here vendor‑risk, credential hygiene, or monitoring for active campaigns—and turn it into a concrete action item for this week. Then, share this roundup internally as your security briefing