India has issued a high-level AI Impact Summit cybersecurity alert ahead of the landmark global gathering, warning that foreign threat actors may attempt to deploy deepfakes, hijack networks, plant malware, and launch ransomware attacks targeting critical infrastructure. This isn’t just routine caution.
Incident Overview: Why the AI Impact Summit Is a Prime Target
According to senior officials, a detailed cybersecurity advisory has already been circulated to ministries, telecom providers, law enforcement agencies, and technical partners involved in the summit.
The warning highlights several specific risks:
- Deepfake manipulation of speeches and public statements
- Wi-Fi network breaches
- Session hijacking during virtual engagements
- Malware infiltration
- Ransomware attacks targeting critical infrastructure
High-profile international events have long been prime targets for cyber activity. What makes this summit different is its focus on AI itself. Threat actors may see an opportunity to demonstrate capability, test digital defenses, or simply create chaos on a global stage.
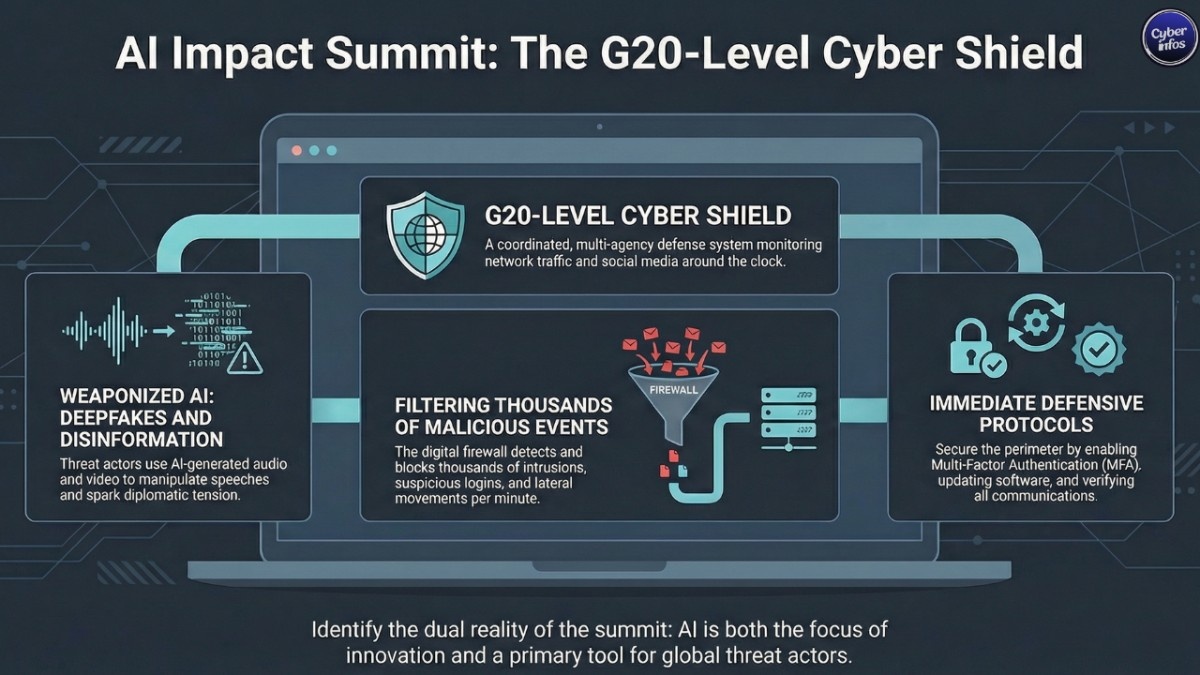
To counter these risks, India has reportedly activated what sources describe as a “G20-level cybersecurity shield.”
In simple terms, this means a coordinated, multi-agency defense system operating around the clock. Cybersecurity experts, ethical hackers, analysts, and auditors are working together to monitor and respond to threats in real time.
Their surveillance includes:
- Social media platforms for misinformation or manipulated videos
- Real-time network traffic
- Vulnerability disclosures
- Suspicious login attempts
- Signs of intrusion or lateral movement inside networks
Sources indicate the system can detect and filter thousands of malicious events per minute essentially acting as a digital firewall around the summit infrastructure.
How the Threats Could Work
Deepfake Manipulation
Deepfakes are no longer obvious, glitchy fakes. Today’s AI-generated video and audio can look and sound disturbingly real.
In the context of the summit, attackers could:
- Release a fabricated video of a leader making controversial remarks
- Slightly alter a live broadcast feed
- Circulate manipulated clips on social media to spark outrage
Imagine someone putting words in a leader’s mouth digitally and millions believing it before fact-checkers catch up. That’s the risk.
Technically, deepfakes rely on advanced AI models trained on hours of video and audio. Once generated, the content can spread across platforms in minutes. Even if it’s debunked later, the damage may already be done.
Network Hijacking and ISP Router Compromise
Another major concern mentioned in the AI Impact Summit cybersecurity alert is router and network-level compromise.
If attackers gain control of ISP routers, they can quietly redirect internet traffic, intercept sensitive communications, or inject malicious code into data streams.
Think of it like someone secretly rerouting your mail, opening it, copying the contents, and resealing it before it reaches you.
Session hijacking during virtual engagements is also a real risk. An attacker could take over an active video conference session, disrupt proceedings, or steal authentication tokens to gain further access.
Malware and Ransomware Attacks
Ransomware remains one of the most disruptive cyber threats globally. If attackers infiltrate summit-related systems, they could encrypt critical data and demand payment for its release.
In a worst-case scenario, critical infrastructure such as telecommunications networks or government systems could be temporarily disrupted to maximize pressure.
Who Is at Risk?
The AI Impact Summit cybersecurity alert primarily focuses on government systems, but the ripple effects could extend much further.
Direct Risk Groups:
- Government ministries and agencies
- Telecom operators and ISPs
- Event organizers and IT vendors
- Media outlets covering the summit
Indirect Risk Groups:
- Businesses relying on shared networks
- Attendees using hotel or public Wi-Fi
- Social media users exposed to manipulated content
Foreign dignitaries and domain experts may also face targeted phishing campaigns disguised as official summit communications. A single compromised credential can open the door to larger network access.
How to Protect Yourself and Your Organization
🔒 Immediate Actions (Do Now)
- Verify All Communications – Confirm summit-related emails through official channels before clicking anything.
- Avoid Unknown USB Devices – Never plug external storage into secure systems.
- Update Software Immediately – Install the latest patches for routers, operating systems, and applications.
- Enable Multi-Factor Authentication (MFA) – Add an extra layer of protection to accounts, especially admin accounts.
🛡 Short-Term Measures (This Week)
- Segment Sensitive Networks – Separate critical systems from general access environments.
- Run Security Audits or Pen Tests – Identify weak spots before attackers do.
- Deploy Deepfake Detection Tools – Use verification systems to authenticate official videos.
- Increase Monitoring – Watch for unusual traffic spikes or login attempts.
🧱 Long-Term Best Practices
- Adopt a Zero Trust Approach – Assume no device or user is automatically trusted.
- Train Staff on Deepfake Risks – Encourage verification before reacting to shocking content.
- Maintain Offline Backups – Ensure ransomware cannot lock your only copy of critical data.
- Prepare an Incident Response Plan – Know exactly who does what during a cyber emergency.
These measures aren’t just for summits they’re essential for modern digital resilience.
Official Response and Preparedness
Authorities stress that the AI Impact Summit cybersecurity alert is preventive, not reactive. Intelligence assessments suggest elevated risk, but officials say the country is fully prepared.
The “G20-level cybersecurity shield” integrates automated detection systems with human oversight. External USB devices are banned on official systems, and enhanced surveillance may temporarily restrict certain network activities.
The message from officials is steady and clear: the threats are real, but so are the defenses.
Additional Safety Tips
- Pause before sharing viral clips. Verify authenticity through official channels.
- Use secure connections. Avoid conducting sensitive work on open public Wi-Fi.
- Strengthen password hygiene. Use unique passwords and a reputable password manager.
Cybersecurity isn’t just about technology it’s about habits.
FAQ: AI Impact Summit Cybersecurity Alert
What is the AI Impact Summit cybersecurity alert?
The AI Impact Summit cybersecurity alert is an official warning from Indian authorities about potential deepfake, ransomware, and network-based attacks targeting the summit.
Why are deepfakes such a serious concern?
Because they can convincingly fabricate statements from world leaders. Even brief manipulated content can spread rapidly and cause confusion or reputational harm.
Could everyday internet users be affected?
Possibly. Indirect impacts such as misinformation campaigns or network disruptions could affect online services and public perception.
How can organizations reduce ransomware risk during major events?
By enabling MFA, maintaining offline backups, segmenting networks, conducting penetration testing, and monitoring systems continuously.
Is India prepared to manage these threats?
Officials state that a multi-layered, G20-level cybersecurity shield is active and capable of detecting and mitigating high-volume cyber threats in real time.
Final Thoughts
The AI Impact Summit cybersecurity alert is a reminder that technological progress and security must evolve together.
Artificial intelligence offers extraordinary opportunities but it also creates new attack surfaces. Deepfake manipulation, ransomware, and network hijacking are not distant possibilities; they are current realities.
By combining advanced monitoring systems with disciplined cyber hygiene, India aims to ensure the summit proceeds without disruption.
The broader lesson is clear: preparedness is power.
Stay Updated
Stay ahead of emerging threats: Join our WhatsApp Channel for real-time security alerts.
Follow us on LinkedIn for daily cybersecurity insights and breaking news.

