If there was one hard lesson the security community absorbed in data breaches 2025, it was that the mechanics of compromise have fundamentally changed.
Data breaches have existed for decades, but data breaches 2025 felt categorically different. The incidents were not only larger, they were more frequent and more evenly distributed across industries. Education, healthcare, aviation, finance, telecom, retail, and cloud-native software providers all suffered major data breaches, often within weeks of one another. There were no safe sectors and no isolated failures.
What distinguished data breaches 2025 was not a surge in zero-day exploits or advanced malware. Instead, attackers leaned heavily on identity-based access. Stolen credentials, abused OAuth tokens, social engineering, and unmonitored SaaS permissions became the dominant entry points. In many of the most damaging cybersecurity incidents 2025, no malware was ever deployed. No firewall rule was bypassed. Attackers authenticated successfully and operated as legitimate users.
Security research published throughout the year consistently showed that credential theft attacks accounted for more than 60 percent of initial access across large-scale data breaches. Ransomware groups refined their playbooks into reliable double-extortion operations, while infostealer malware quietly fueled an underground economy of credentials and session tokens. By the end of the year, data breaches 2025 no longer appeared as individual failures, but as symptoms of systemic exposure.
How This List Was Compiled
This Year in Review analyzes the biggest data breaches of 2025 using criteria designed to emphasize learning value rather than shock value.
Each incident was evaluated based on:
- Scale of exposure, including individuals, enterprises, or entire platforms
- Sensitivity of compromised data, ranging from credentials and PII to PHI and telecom identity material
- Verification, through regulatory disclosures, breach notifications, court filings, or credible security research
- Strategic relevance, focusing on incidents that highlight broader trends in identity-based attacks and cloud risk
Sources include government disclosures, investigative reporting, breach notifications, and independent analysis. The intent is not to sensationalize large-scale data breaches, but to understand why they continue to occur and how defenders can adapt.
The 10 Biggest Data Breaches of 2025

1. 16 Billion Credential Compilation Leak — 2025
What happened:
One of the most consequential data breaches 2025 was not tied to a single company. Instead, researchers uncovered a compilation of roughly 16 billion usernames and passwords aggregated from years of credential theft attacks. The dataset drew from infostealer malware logs, phishing campaigns, and previously disclosed breaches.
The result was a global account takeover resource that amplified risk across consumer platforms, enterprise SaaS environments, and cloud services.
Type of breach: Credential aggregation
Data exposed: Usernames, emails, passwords
Impact: Global, cross-platform account takeover risk
Root cause: Password reuse and long-running credential theft attacks
Key lesson: Password-only authentication should be considered insufficient by default.
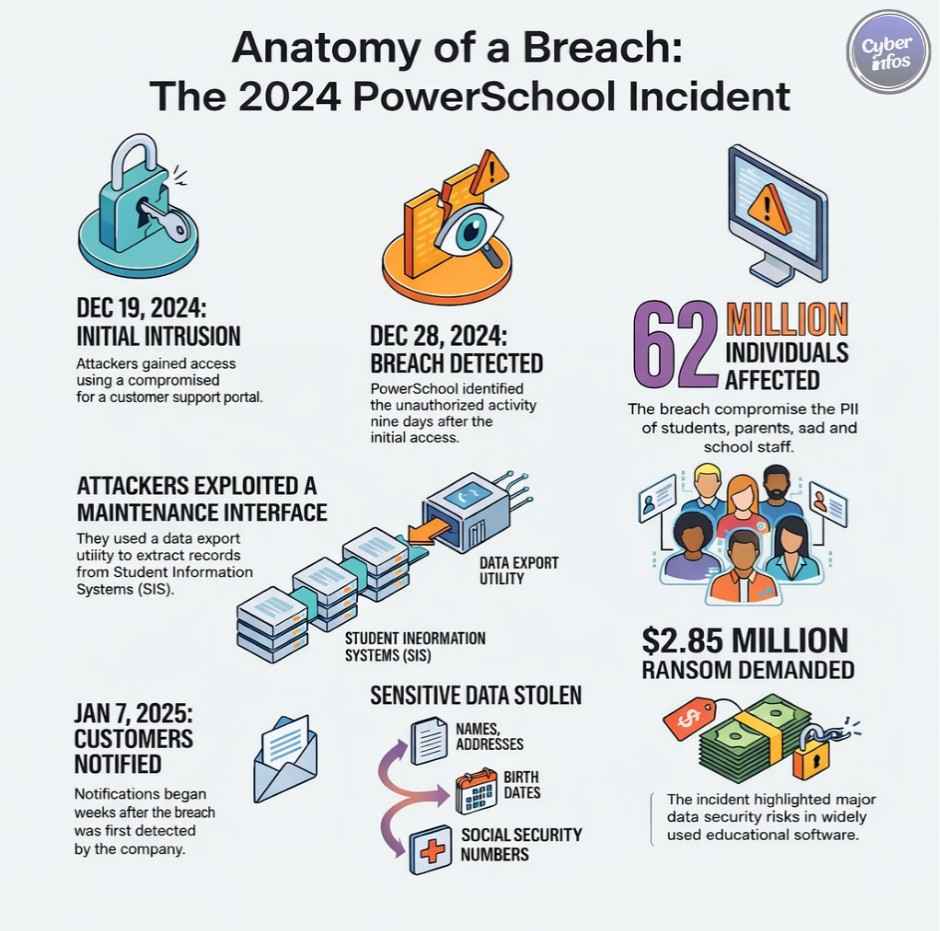
2. PowerSchool Data Breach — December 2024 / 2025 Disclosure
What happened:
Attackers gained access to PowerSchool’s PowerSource support portal using a compromised credential. The portal’s deep integration with customer environments transformed a single access point into one of the largest major data breaches affecting the education sector.
Type of breach: Credential compromise
Data exposed: PII, Social Security numbers, student records
Impact: Approximately 62 million individuals
Root cause: Over-trusted support access
Key lesson: Identity governance must extend to support and administrative tooling.
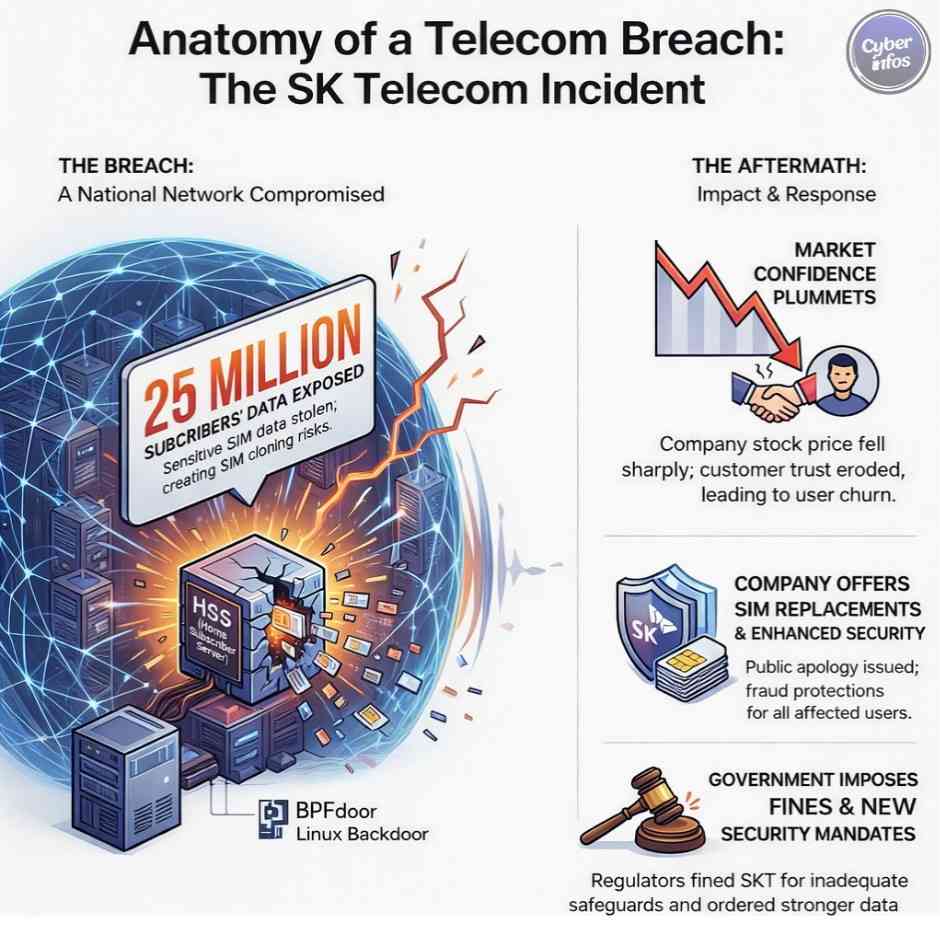
3. SK Telecom USIM Breach — April 2025
What happened:
In April, SK Telecom disclosed a breach involving its Home Subscriber Server, a core authentication system underpinning mobile identity. This incident ranked among the most severe cybersecurity incidents 2025 due to its implications for national-scale telecom security.
Type of breach: Core infrastructure compromise
Data exposed: USIM and SIM authentication data
Impact: Approximately 25 million subscribers
Root cause: Undisclosed access weakness
Key lesson: Telecom identity systems require infrastructure-grade protection.
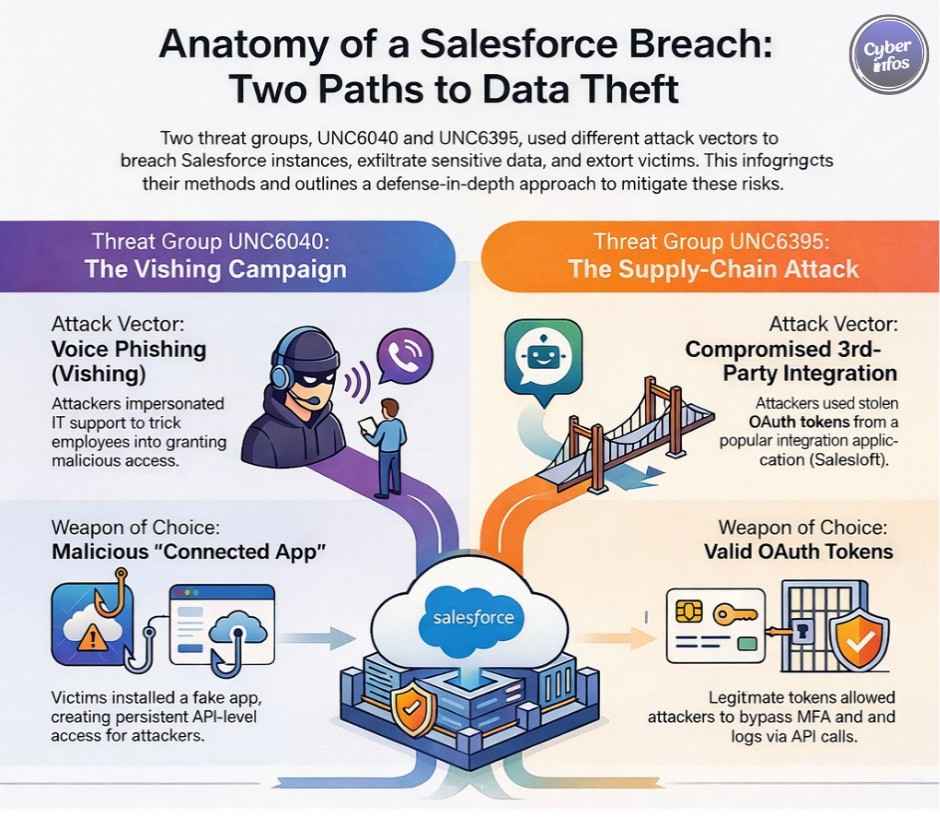
4. Salesforce OAuth Data Theft Campaigns — 2025
What happened:
Multiple threat groups conducted coordinated campaigns abusing OAuth trust relationships within Salesforce environments. These SaaS security incidents relied on voice phishing and malicious app approvals rather than credential brute force.
Type of breach: OAuth abuse
Data exposed: CRM data, API tokens, cloud credentials
Impact: Hundreds of organizations
Root cause: Over-permissive OAuth scopes
Key lesson: OAuth abuse is now a primary vector in cloud security breaches.
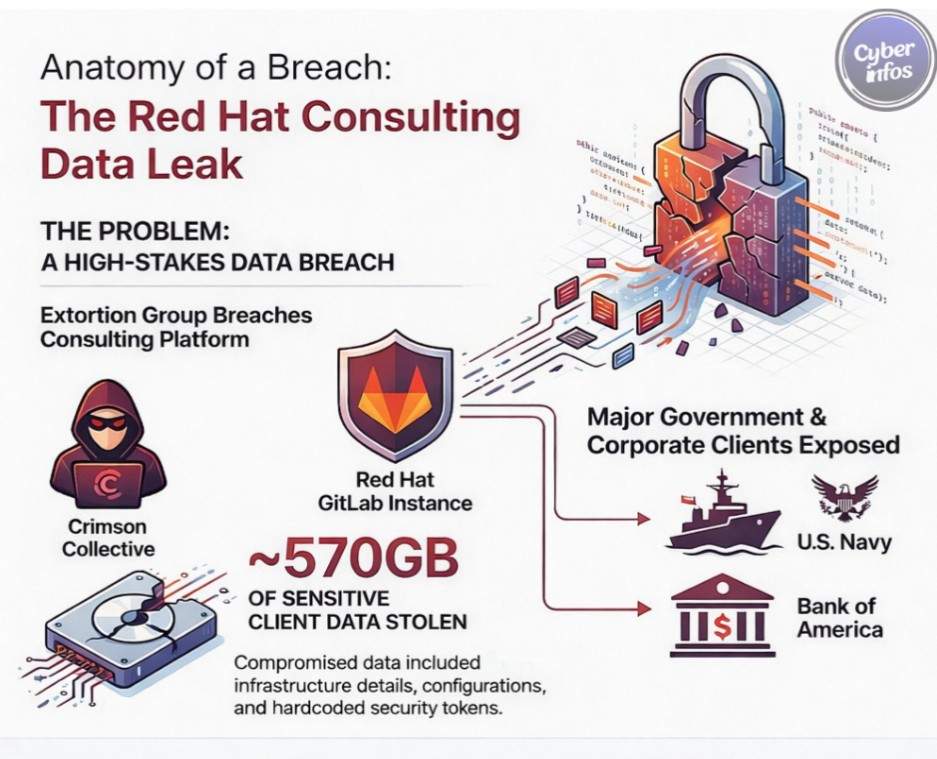
5. Red Hat Consulting GitLab Breach — October 2025
What happened:
Attackers breached a GitLab instance used by Red Hat consulting services and exfiltrated hundreds of gigabytes of sensitive material. Although not a production system, the breach created downstream risk for clients, placing it among the most instructive data breaches 2025.
Type of breach: Development platform compromise
Data exposed: Tokens, secrets, internal documentation
Impact: Enterprise and government clients
Root cause: Hardcoded credentials
Key lesson: Non-production systems can drive production-level exposure.
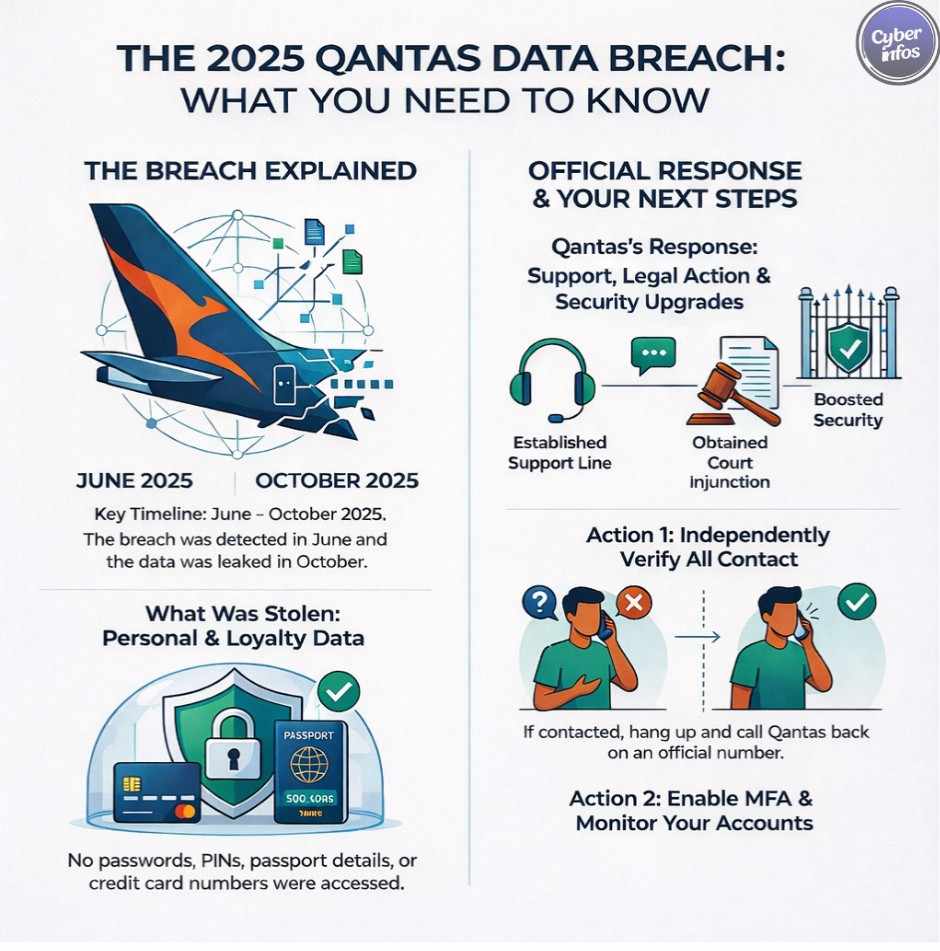
6. Qantas Customer Data Breach — June–October 2025
What happened:
Attackers targeted a third-party call center supporting Qantas and socially engineered access to a Salesforce CRM. The incident underscored how identity-based attacks exploit human workflows rather than technical flaws.
Type of breach: Third-party CRM compromise
Data exposed: PII and loyalty data
Impact: Approximately 5.7 million customers
Root cause: Social engineering
Key lesson: Call centers are high-risk SaaS access points.

7. Allianz Life CRM Breach — July 2025
What happened:
This breach originated entirely within a third-party SaaS platform used by Allianz Life. No internal systems were compromised, reinforcing a broader trend in cloud security breaches where vendors become the weakest link.
Type of breach: Third-party SaaS compromise
Data exposed: PII and potential SSNs
Impact: Approximately 1.4 million customers
Root cause: Weak vendor identity controls
Key lesson: SaaS access must be continuously monitored.
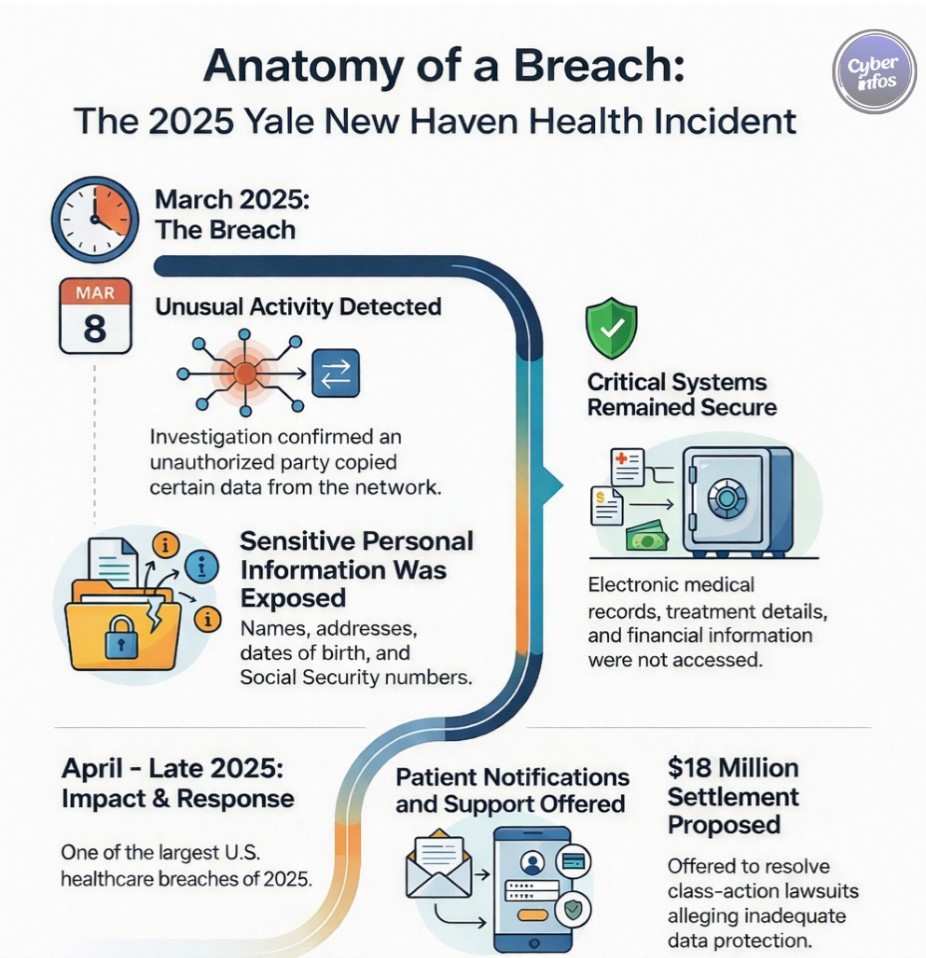
8. Yale New Haven Health System Breach — March 2025
What happened:
Unauthorized access within Yale New Haven Health’s IT environment led to exposure of patient data. Like many healthcare large-scale data breaches, identity compromise persisted undetected within a complex system landscape.
Type of breach: Network intrusion
Data exposed: PII and Social Security numbers
Impact: Approximately 5.5 million patients
Root cause: Identity misuse
Key lesson: Healthcare identity failures create permanent risk.
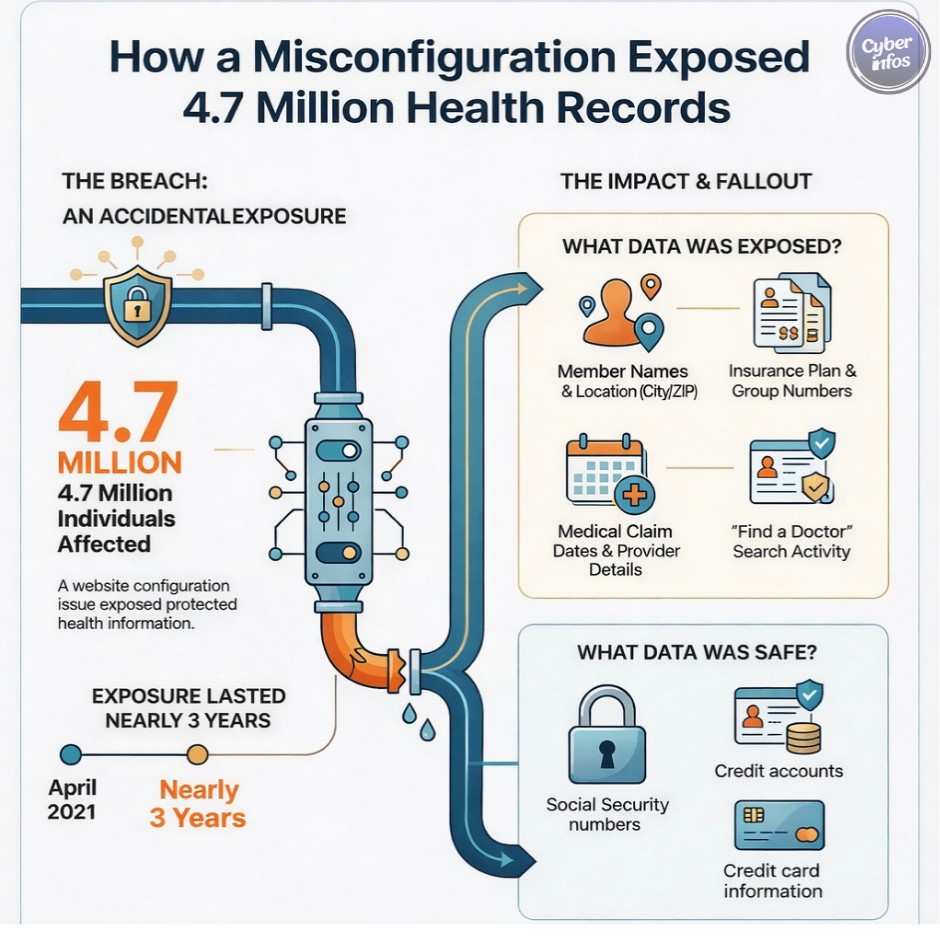
9. Blue Shield of California Analytics Exposure — 2025
What happened:
A misconfigured analytics setup shared sensitive member data with advertising platforms over several years. This incident illustrates how cloud security breaches can occur without attackers—simply through misconfiguration.
Type of breach: Configuration error
Data exposed: PHI and insurance metadata
Impact: Approximately 4.7 million members
Root cause: Unreviewed data flows
Key lesson: Analytics tools require the same scrutiny as core systems
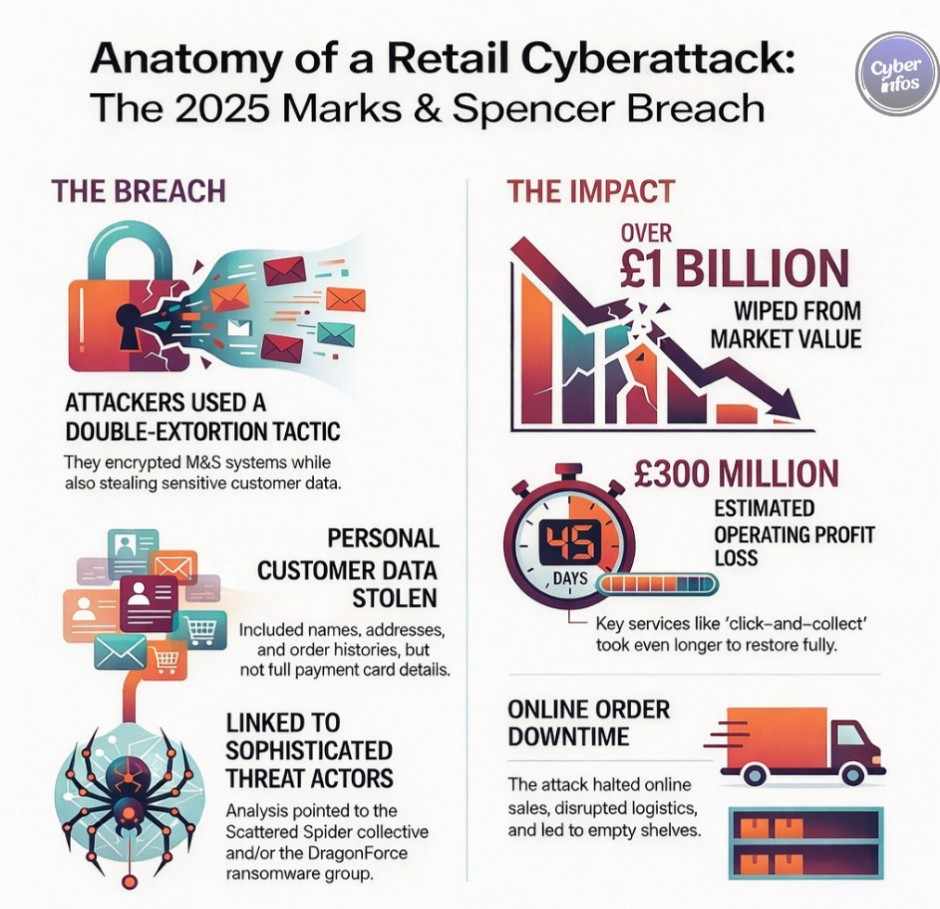
10. Marks & Spencer Ransomware Attack — April 2025
What happened:
Marks & Spencer suffered a ransomware attack that encrypted systems and exfiltrated customer data. As with many ransomware attacks 2025, credential theft enabled initial access before encryption and extortion.
Type of breach: Ransomware with double extortion
Data exposed: Customer PII
Impact: £300M+ in losses
Root cause: Credential compromise
Key lesson: Retail remains a prime ransomware target.
Common Patterns Behind 2025’s Biggest Data Breaches
Across the biggest data breaches of 2025, several patterns repeated:
- Identity-based attacks replaced exploit-driven intrusion
- Credential theft attacks dominated initial access
- OAuth abuse fueled SaaS security incidents
- Cloud security breaches often went unnoticed
- Third-party access expanded blast radius
Attackers did not bypass controls. They authenticated.
What Organizations Can Learn From These Breaches
To reduce exposure in future data breaches 2025-style incidents, organizations should prioritize:
- Zero trust and least privilege
- Phishing-resistant MFA and passkeys
- Continuous monitoring of identity and API activity
- Strong governance of SaaS security incidents
- Ongoing cloud configuration audits
Modern defense is no longer perimeter-first. It is identity-first.
What to Expect in 2026: Future Cybersecurity Risks
Based on trends observed in data breaches 2025, organizations should expect:
- AI-enhanced phishing and identity-based attacks
- More ransomware attacks targeting SaaS ecosystems
- Increased abuse of OAuth and API trust
- Faster, automated credential exploitation
The attack surface will continue shifting toward identity.
Final Thoughts: Why Data Breaches Keep Growing
Data breaches 2025 demonstrated that the problem is not weak tools or careless teams. It is structural. Digital ecosystems are interconnected, identity is universal, and trust scales faster than control.
When identity fails, everything connected to it is exposed. The organizations that succeed beyond data breaches 2025 will be those that treat identity as core infrastructure designed, governed, and defended with the same rigor once reserved for networks and endpoints.

