This cybersecurity weekly report incident happens 21 to 27 December 2025 brings together the most consequential security developments disclosed this week, as attackers exploited newly published flaws, revived older vulnerabilities, and abused trusted software distribution channels. According to multiple security firms, no single incident dominated headlines. Instead, defenders faced simultaneous failures across databases, browser extensions, open-source packages, and legacy infrastructure.
Researchers said attackers continued to move faster than patches, exploiting gaps within hours of disclosure. Several incidents also showed that damage from past breaches is still unfolding years later, raising concerns about long-term exposure risks as organizations enter 2026.
Threat of the Week in This Cybersecurity Weekly Report
MongoDB Vulnerability Actively Exploited
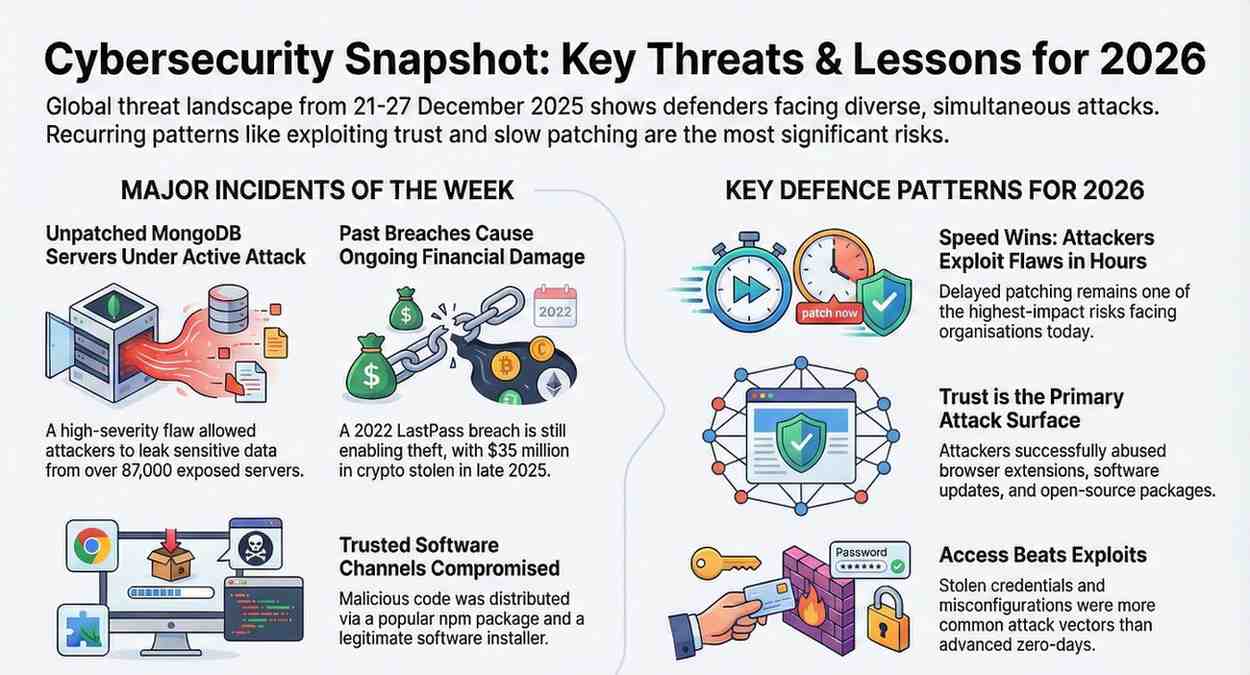
The most urgent issue highlighted in this cybersecurity weekly report is the active exploitation of CVE-2025-14847, a high-severity vulnerability affecting MongoDB. According to cloud security firm Wiz, the flaw allows unauthenticated attackers to leak sensitive data directly from server memory.
Attack surface monitoring company Censys reported that more than 87,000 MongoDB instances remain potentially exposed worldwide, with concentrations in the United States, China, Germany, India, and France. MongoDB released patched versions this week and urged customers to upgrade immediately. The company has not yet disclosed technical details about in-the-wild exploitation, citing ongoing investigations.
Top Security Incidents Covered in the Cybersecurity Weekly Report
Trust Wallet Chrome Extension Incident
Trust Wallet confirmed this week that a malicious update to its Chrome browser extension led to approximately $7 million in losses. According to the company, attackers published a compromised version using a leaked Chrome Web Store API key. Trust Wallet stated that mobile users were not affected and said it is reimbursing impacted customers.
DNS Poisoning Campaign Delivers Malware
Kaspersky researchers attributed a long-running espionage campaign to the China-linked group known as Evasive Panda. According to the firm, attackers poisoned DNS responses to deliver trojanized software updates that installed the MgBot backdoor. The activity targeted victims in Türkiye, China, and India between 2022 and 2024.
LastPass Breach Fallout Continues
Blockchain analytics firm TRM Labs reported this week that attackers are still exploiting data stolen during the 2022 LastPass breach. According to the report, weak master passwords enabled criminals to decrypt vault backups and steal at least $35 million in cryptocurrency as recently as late 2025.
Fortinet Warns of Renewed Exploitation
Fortinet confirmed renewed abuse of CVE-2020-12812, a flaw that can allow users to bypass multi-factor authentication under specific configurations. The company advised customers to review authentication logs and reset credentials if suspicious activity is detected.
Supply Chain and Developer Risks
This cybersecurity weekly report also highlights growing risks within developer ecosystems. According to security firm Koi, a malicious npm package posing as a WhatsApp API library was downloaded more than 56,000 times before removal. Researchers warned that uninstalling the package does not revoke attacker access unless users manually unlink devices.
Separately, Emurasoft disclosed that its EmEditor installer download link was altered in a 2022 breach that is only now coming to light. According to Chinese security firm QiAnXin, the malicious installer delivered an infostealer capable of harvesting credentials and browser data.
Trending Vulnerabilities Identified This Week
Security researchers observed rapid scanning and exploitation attempts targeting newly disclosed flaws. According to multiple vendors, attackers prioritized vulnerabilities that required no authentication and affected widely deployed software.
This cybersecurity weekly report notes that several CVEs disclosed this week showed signs of abuse within hours, reinforcing concerns about shrinking remediation windows for defenders.
Law Enforcement and Global Threat Activity
Coinbase CEO Brian Armstrong confirmed this week that Indian authorities arrested a former customer support contractor accused of selling user data to hackers. Court documents indicate the breach affected nearly 70,000 individuals. Coinbase stated that it has since tightened vendor controls.
Meanwhile, threat intelligence firm Intrinsec identified a Russian cybercriminal known as “Fly” as a likely administrator of the Russian Market credential marketplace, according to infrastructure and account analysis.
Why This Cybersecurity Weekly Report Matters
According to analysts, the incidents outlined in this cybersecurity weekly report reveal consistent patterns: attackers favor trusted access paths, older breaches continue to generate losses, and patch delays remain a primary risk factor.
Security teams are advised to prioritize vulnerability management, audit third-party access, and reassess assumptions about breach containment timelines.
Emerging Patterns to Carry Into 2026
Looking across the week’s events, several consistent themes emerge:
-
Speed wins
Attackers routinely exploit vulnerabilities before organizations complete patch cycles. Delayed updates remain one of the highest-impact risks. -
Trust is the primary attack surface
Browser extensions, update mechanisms, DNS infrastructure, and open-source packages were all abused. Technical controls failed where trust assumptions went unchallenged. -
Old incidents never truly end
Data stolen years ago continues to generate financial and operational damage. Encryption alone does not eliminate long-term risk. -
Access beats exploits
Stolen credentials, insider cooperation, and misconfigurations were more common than advanced zero-days. -
Detection must extend beyond malware
Many incidents involved no traditional malware at all, relying instead on legitimate tools used maliciously.
Looking Ahead
As this cybersecurity weekly report closes out 2025, researchers say the signals are clear. The threat landscape is not defined by isolated catastrophes but by repeated, preventable failures. How organizations respond to these patterns will shape their security posture in 2026.