For years, security researchers have warned that generative AI would eventually move beyond phishing emails and scripted scams and become embedded directly inside live malware. That shift no longer feels theoretical.
A newly discovered strain called PromptSpy Android malware is the first documented example of Android malware using generative AI during runtime execution. Rather than relying entirely on hardcoded logic, it consults Google’s Gemini model mid-operation to determine how to stay persistent on an infected device.
It’s not cinematic. It’s not dramatic. But it is meaningful.
Discovered in February 2026 by researchers at ESET, PromptSpy integrates AI in a focused and deliberate way—solving a persistence challenge that has historically required device-specific scripting. That practical use of AI signals a broader evolution in how mobile threats may develop from here.
Incident Overview: Discovery of PromptSpy Android Malware
ESET researchers identified two related Android malware variants earlier this year. The first, initially named VNCSpy, appeared on VirusTotal in January 2026 with samples uploaded from Hong Kong. A second, more advanced version surfaced in February from Argentina.
The later strain introduced generative AI integration and was subsequently named PromptSpy.
At this time, researchers have not confirmed widespread infections in telemetry. However, associated domains were reportedly used to impersonate JPMorgan Chase, suggesting the malware may have been distributed beyond controlled testing environments.
Whether proof-of-concept or limited deployment, PromptSpy Android malware demonstrates that Android malware using generative AI is no longer theoretical.
How Google Gemini Malware Abuse Enables Persistence
Generative AI in Android Malware Execution
On many Android devices, users can “pin” or “lock” an app in the Recent Apps screen. When pinned, the operating system is far less likely to terminate that app during memory cleanup.
For legitimate applications, this preserves background processes. For spyware, it creates resilience.
The complication for attackers is fragmentation. The process for pinning apps differs across manufacturers and Android skins. Traditional scripts often fail when UI layouts vary.
This is where Google Gemini malware abuse becomes central to PromptSpy’s design.
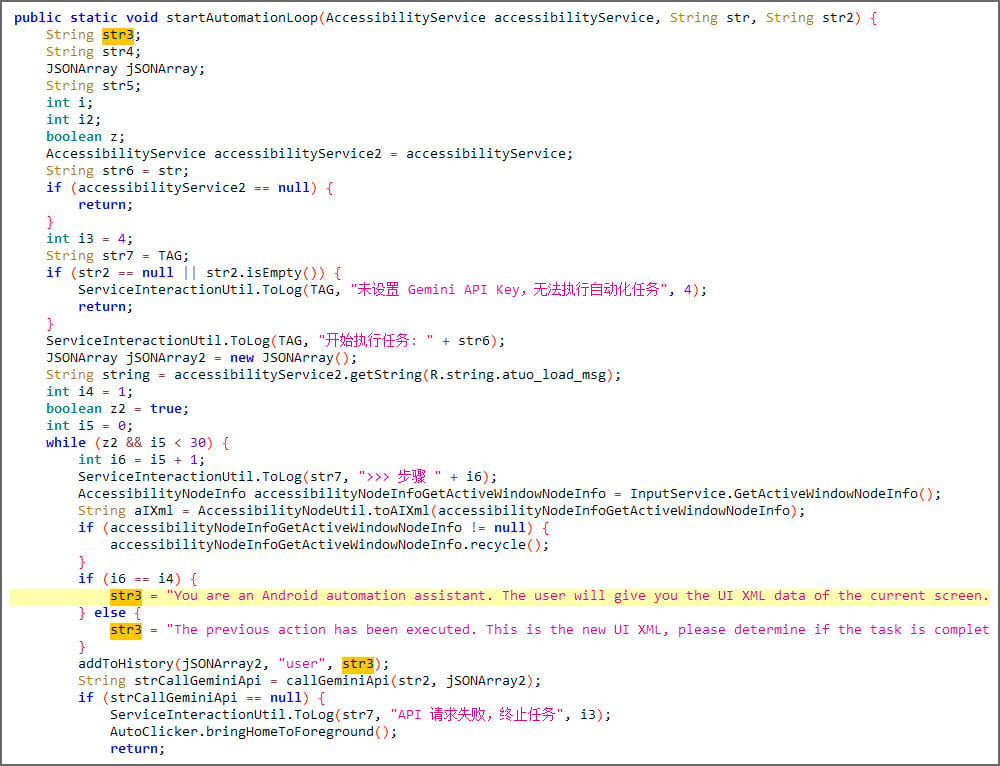
The malware collects:
- An XML dump of the current screen
- Visible UI elements and labels
- Class identifiers
- Screen coordinates
It then sends this structured data to Gemini. The AI model responds with JSON-formatted instructions describing which UI element should be tapped to successfully pin the app.
PromptSpy executes the instruction using Android’s Accessibility Service, checks the updated screen, and repeats the process until the app is locked into place.
Instead of predicting every interface variation, the malware asks the AI what to do next. That adaptive loop is what sets this AI-powered Android spyware apart from earlier threats.
Capabilities of This AI-Powered Android Spyware
The generative AI component focuses on persistence. The rest of PromptSpy functions as a full-featured spyware platform.
It contains a built-in VNC module that enables remote viewing and control once Accessibility permissions are granted.
According to ESET, PromptSpy can:
- Upload a list of installed apps
- Intercept lockscreen PINs and passwords
- Record pattern unlock screens as video
- Capture screenshots on demand
- Record screen activity and gestures
- Report the current foreground application
For individuals, that exposure includes banking apps, authentication tools, and private communications. For small businesses particularly those allowing BYOD access the risk extends to cloud dashboards, email platforms, and internal systems.
The spyware functionality is conventional. The adaptive persistence is not.
Anti-Removal and Evasion Techniques
PromptSpy actively resists removal attempts.
When users try to uninstall the app or disable Accessibility permissions, the malware overlays transparent rectangles over buttons labeled:
- Stop
- End
- Clear
- Uninstall
The interface appears unchanged. But taps are intercepted.
The recommended removal method is to reboot into Android Safe Mode, which disables third-party applications and prevents the malware from blocking its own uninstall process.
Overlay abuse combined with Android Accessibility malware persistence creates a layered defense that can frustrate even technically literate users.
Who Is Most at Risk?
Although confirmed distribution appears limited, several groups face higher exposure:
- Users installing apps from unofficial domains
- Mobile banking customers
- Cryptocurrency wallet holders
- Remote employees using unmanaged Android devices
- Small businesses without mobile device management (MDM)
More broadly, PromptSpy illustrates how generative AI in cybersecurity threats is moving from experimentation to practical implementation.
Google Threat Intelligence recently reported that state-aligned threat actors are incorporating AI tools throughout attack lifecycles. PromptSpy differs in one key respect it integrates AI directly into malware execution logic.
Protection & Mitigation Strategies
Despite its AI-assisted behavior, the defensive fundamentals remain consistent:
- Avoid sideloading apps from unknown sources
- Review Accessibility permissions regularly
- Enable Google Play Protect
- Install Android updates promptly
- Deploy MDM solutions in business environments
- Reboot into Safe Mode if uninstall attempts fail
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) continues to recommend limiting application permissions and monitoring for abnormal device behavior.
No adaptive malware can override disciplined security hygiene.
Why PromptSpy Signals a Shift
PromptSpy Android malware does not represent an AI takeover of cybersecurity. The AI integration is narrow and targeted.
But that narrow integration proves something important: attackers are comfortable embedding generative models into live malware workflows.
If AI use expands into evasion logic, adaptive phishing overlays, or environment-aware payload delivery, detection strategies will need to evolve accordingly.
For now, PromptSpy stands as a milestone an early indicator that Android malware using generative AI is technically viable and operationally practical.
FAQ: PromptSpy Android Malware
What is PromptSpy Android malware?
PromptSpy Android malware is a spyware family that integrates Google’s Gemini model into its runtime behavior to adapt its persistence technique across different Android devices.
How does Android malware using generative AI work?
The malware sends structured screen data to Gemini and receives instructions on which UI elements to interact with, allowing adaptive app pinning and persistence.
Is Google responsible for this threat?
No. This represents Google Gemini malware abuse by threat actors. The AI model itself is not compromised but misused through standard access.
Are generative AI cybersecurity threats increasing?
Yes. Security researchers report growing experimentation with AI tools for reconnaissance, automation, and now runtime behavioral adaptation.
How can I remove PromptSpy Android malware?
Reboot into Android Safe Mode, uninstall the suspicious application, and revoke Accessibility permissions before restarting normally.
Final Thoughts
The discovery of PromptSpy Android malware marks a practical turning point. Generative AI is no longer limited to supporting cybercrime at the edges it is beginning to influence how malware behaves in real time.
Today, the AI handles one task: adaptive persistence. Tomorrow, it could assist in evasion or automated social engineering.
For users and organizations alike, the message is steady rather than sensational. Keep devices updated. Audit permissions. Deploy mobile security controls where appropriate. Generative AI in cybersecurity threats has entered an operational phase. PromptSpy simply makes that shift visible.