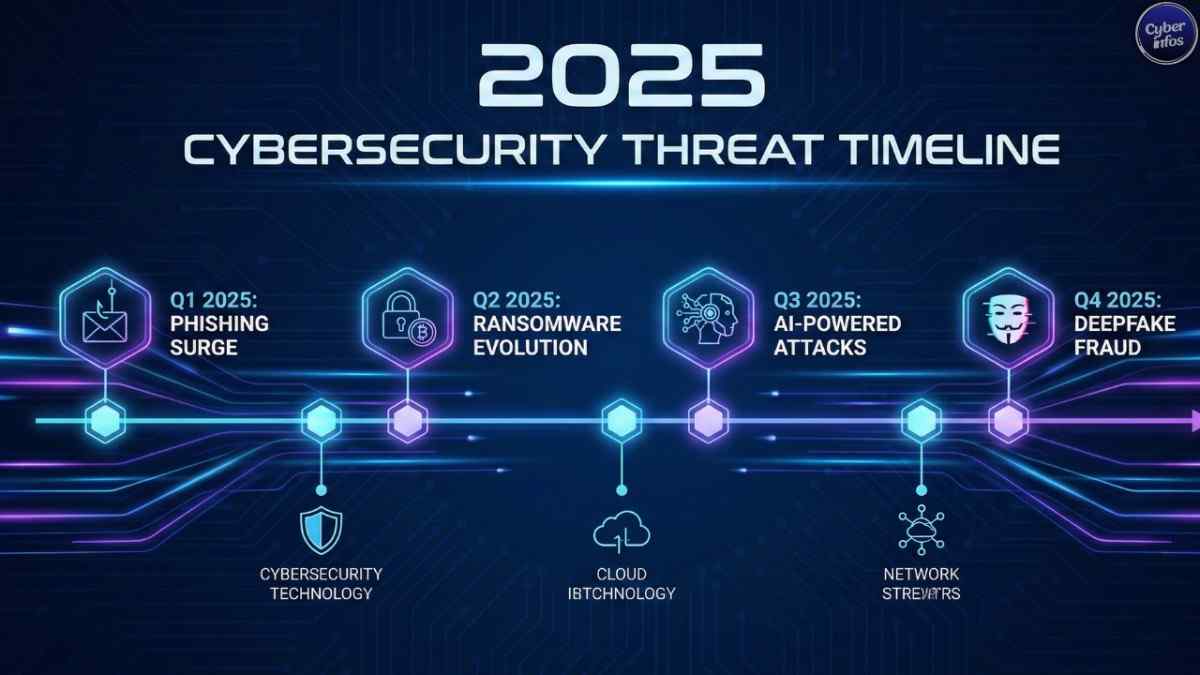
The rise of web security threats 2025 pushed organizations to reassess nearly every assumption they had about online protection. This year’s attacks weren’t just faster—they were more adaptive, more automated, and far more disruptive than experts expected.
With AI-driven exploits, widespread JavaScript injection, and deep supply-chain compromises unfolding at scale, it became clear that older defense models could no longer keep up. This guide breaks down the five threats that reshaped the security landscape in 2025 and the lessons they leave behind for the future.
Vibe Coding Vulnerabilities: When AI Starts Writing Your Bugs
The surge of AI-generated development—known as vibe coding—defined 2025, but the speed it introduced came with a serious downside: quietly embedded vulnerabilities that were easy to miss and hard to detect.
What Made Vibe Coding So Dangerous
- AI produces code that works, not necessarily code that’s secure
- Developers often assume the AI handled validation
- Traditional scanners struggle to flag deeper semantic flaws
Stats that hit hard:
- 45% of AI-generated code contained exploitable weaknesses
- A 70% vulnerability rate appeared in Java AI-generated code
- Major dev tools suffered critical CVEs like CurXecute, EscapeRoute, and Claude Code’s DNS exfiltration bug
Real-World Damage
- Replit’s AI assistant accidentally wiped a live production database
- A fintech startup experienced an authentication bypass
- AI-written login logic left room for silent injection vectors
How Enterprises Responded
- Security-first prompting became standard
- Multi-step validation replaced one-shot code generation
- Behavioral monitoring caught anomalies like odd API calls and serialization quirks
- The EU AI Act added new guardrails for high-risk AI systems
JavaScript Injection at a Scale the Web Has Never Seen
JavaScript remains the backbone of the modern web, and in 2025 attackers exploited it more aggressively than ever.
The Largest Injection Campaign in History
- Over 150,000 websites were compromised
- Attackers replaced real interfaces with full-screen gambling overlays
- Techniques evolved from the Polyfill.io compromise that hit major brands like Hulu and Mercedes-Benz
Impact of JavaScript Injection Threats
- React’s built-in XSS protections weren’t enough
- Prototype pollution enabled deep DOM manipulation
- More than 50,000 banking sessions were hijacked
- Over 22,000 CVEs were tied to JavaScript-related vulnerabilities
Defensive Shifts in 2025
- Rigid output-context encoding became essential:
- HTML encoding
- JavaScript escaping
- URL encoding
- Behavioral analytics flagged suspicious POST behavior
- Organizations tightened control over third-party libraries
Magecart & E-Skimming 2.0 — The Silent Financial Data Theft Boom
Magecart attacks didn’t just return—they evolved, using smarter, more selective tactics that slipped past traditional defenses.
Why Magecart Exploded Again
- E-skimming incidents spiked 103%
- Attackers leaned on DOM shadows, geofencing, and WebSockets
- Some malware intentionally paused when DevTools was open
Real-World Attacks
- High-profile brands like British Airways, Ticketmaster, and Newegg were hit
- Modernizr was weaponized across countless stores
- AI-enhanced skimmers targeted buyers more likely to make luxury purchases
The cc-analytics[.]com Incident
- A year-long skimming campaign quietly harvested card data
- The JavaScript was heavily obfuscated
- Thousands of online retailers were exposed
Updated Defense Strategy
- CSPs lost reliability as attackers compromised trusted sources
- PCI DSS 4.0.1 added strict requirements for monitoring all scripts touching payment data
- Behavioral analysis proved more effective than trusting script origins
AI Supply Chain Attacks: The New Dominant Exploit Class
Supply-chain compromises accelerated sharply in 2025 as AI gave attackers the ability to scale, mutate, and personalize malware with unprecedented speed.
Why 2025 Was the Breaking Point
- Malicious package uploads grew by 156%
- Polymorphic malware rewrote itself to bypass detection
- Fake packages appeared credible thanks to AI-generated docs and tests
Key Incidents
- Solana Web3.js saw up to $190k stolen
- AI-generated malware extended detection times to 276 days
- Sandbox-aware malware learned to evade static analysis
The Shai-Hulud Worm
- Infected more than 500 npm packages
- Spread into 25,000+ GitHub repositories
- Used AI-crafted Bash scripts marked with emojis
- Evaded leading AI security tools, which misclassified it as safe
How Organizations Adapted
- AI-focused detection tools became necessary
- Contributor identity verification reduced impersonation
- Zero-trust runtime checks secured CI/CD pipelines
- Dependency provenance tracking grew into a standard practice
Web Privacy Validation: The New Compliance Battleground
Privacy failures became a serious security concern as companies repeatedly broke compliance without realizing it.
The Privacy Reality Check
- 70% of major U.S. websites failed to honor opt-out requests
- Tracking pixels captured sensitive data without consent
- Routine updates caused consent systems to silently break
Major Incidents
- A €4.5M fine for improper email-tracking behavior
- HIPAA issues caused by analytics scripts pulling patient data
- Capital One’s case redefined pixel tracking as “data exfiltration”
Why This Became a Security Issue
Privacy increasingly intersects with security because:
- Leaked data carries legal and regulatory fallout
- Tracking pixels expand the attack surface
- Third-party scripts often behave unpredictably
Modern Privacy Defense
- Continuous consent validation replaced periodic checks
- Real-time monitoring detected misconfigured or rogue scripts
- Automated tools identified policy drift before audits
- Privacy and security functions began merging operationally
Proactive Defense: The Only Winning Strategy Going Into 2026
The consistent lesson across all web security threats 2025 is straightforward: reacting isn’t enough. By the time a threat becomes visible, the damage is usually done.
Common Traits of High-Maturity Security Teams
- They assume breach as a reality
- They rely on continuous validation, not snapshots
- They implement AI-aware defenses across the stack
2026 Readiness Checklist
Use this checklist to gauge how prepared your organization truly is.
Critical Validations
- Map and monitor every third-party dependency
- Apply runtime behavioral monitoring
- Treat AI-generated code as untrusted until reviewed
- Validate consent and data-collection settings in live environments
- Replace quarterly audits with real-time oversight
Final thoughts
The evolving landscape of web security threats 2025 showed that older, reactive security methods can’t handle modern AI-driven risks. With JavaScript injection campaigns, supply-chain compromises, and privacy failures growing more complex, organizations must shift toward continuous validation and behavior-based monitoring. Those willing to modernize their defenses now will be far better positioned in 2026, while those who delay will inevitably face costly breaches they didn’t see coming.
Frequently Asked Questions (FAQs)
1. What are the most serious web security threats 2025 introduced?
The most serious web security threats 2025 introduced include AI-generated code flaws, widespread JavaScript injection, advanced Magecart skimming, supply-chain compromises powered by AI, and large-scale privacy validation gaps.
2. Why did vibe coding increase web security threats 2025?
Vibe coding expanded web security threats 2025 because AI-generated code often lacked strong validation, secure defaults, and proper authentication controls.
3. How can companies defend against web security threats 2025 involving JavaScript injection?
To counter web security threats 2025 involving JavaScript injection, companies must use output-context encoding, audit third-party scripts, and apply behavioral monitoring to detect suspicious script behavior.
4. Did Magecart attacks contribute significantly to web security threats 2025?
Yes, Magecart activity played a major role in web security threats 2025, affecting thousands of e-commerce environments with stealthy and highly targeted skimmers.
5. How do AI-driven supply chain attacks impact web security threats 2025?
AI-driven supply-chain attacks intensified web security threats 2025 by creating malware variants that constantly evolved, making them extremely difficult to detect with static tools.