Flickr has confirmed a potential data breach involving a third-party email service provider, raising concerns that user account metadata may have been exposed. While there is no evidence of a direct compromise of Flickr’s core systems, the incident could still affect a significant portion of its user base estimated at around 35 million monthly users.
The incident was disclosed on 5 February 2026, with public reporting emerging over 5–6 February. Flickr says it acted quickly after being alerted, but investigations are still ongoing.
Below is a clear breakdown of what happened, what data is at risk, and what users should do next.
What happened in this data breach ?
According to Flickr, the company was notified of a vulnerability in a system operated by one of its external email service providers on 5 February 2026.
The flaw may have allowed unauthorized access to some Flickr user information processed or stored by that provider.
Flickr says it disabled access to the affected system within hours.
An internal investigation and third-party review are now underway.
Importantly, Flickr stresses this was a supply-chain issue, not a breach of Flickr’s own production databases.
At this stage, the incident is being described as a potential data exposure, not a confirmed large-scale data theft.
What data may have been exposed
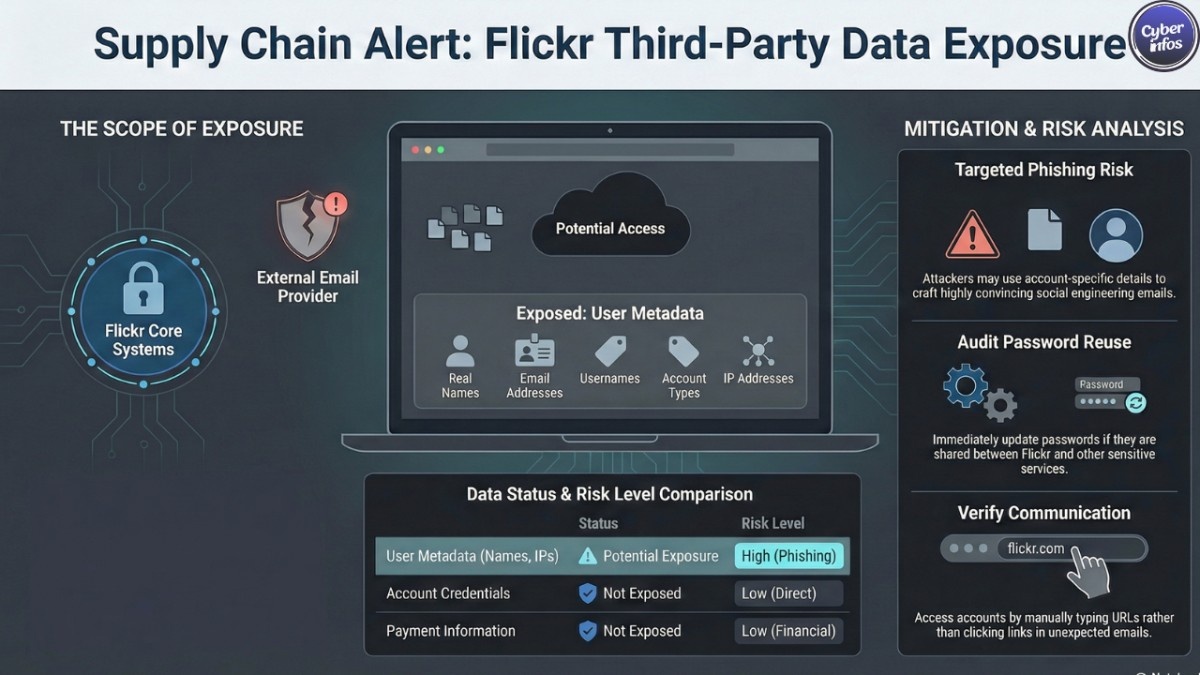
Based on Flickr’s user notifications and security reporting, the following information may have been accessible:
- Real name (member name)
- Email address
- Flickr username
- Account type (Free or Pro)
- IP addresses
- General location inferred from IP
- Platform activity and usage metadata
What was not exposed
Flickr and independent reports consistently state that:
- Passwords were not exposed
- Payment card details were not exposed
While this limits direct financial risk, the exposed data set is still highly valuable for phishing and impersonation attacks.
Does this really affect “35 million users”?
Not necessarily — at least not yet.
Flickr reports approximately 35 million monthly active users, but:
- Flickr has not confirmed how many accounts were actually accessed or affected.
- Official says the flaw “may have allowed unauthorized access to some member information.”
- No specific victim count has been disclosed.
This means headlines claiming “35 million users breached” represent a worst-case scenario, not a confirmed scope.
A more accurate framing is:
Flickr discloses potential third-party data exposure; millions of users advised to remain vigilant.
Why this still matters: real-world risks
1. Highly targeted phishing scams
Attackers could send convincing fake Flickr or SmugMug emails, using:
- Your real name
- Your Flickr username
- Accurate account references (Free vs Pro)
- Location-aware timing
Common lures may include:
- “Copyright infringement” warnings
- Fake password reset notices
- Pro subscription renewal alerts
2. Account takeover via password reuse
If you reuse passwords across services, attackers may attempt credential stuffing, even though Flickr passwords were not leaked.
3. Privacy profiling
IP and activity metadata can be used to:
- Infer location patterns
- Correlate identities across platforms
- Enhance social-engineering attacks
What Flickr users should do right now
1. Be extremely cautious with emails
Do not click links in unexpected Flickr-related emails.
Be wary of urgency, threats, or requests to “verify” your account.
Access your account only by manually typing flickr.com into your browser.
Flickr states it will never ask for your password via email.
2. Change reused passwords immediately
Even as a precaution:
- If your Flickr password is reused anywhere else, change it everywhere.
- Use a unique, long password for Flickr.
- A password manager can help prevent reuse going forward.
3. Strengthen account security
- Verify your recovery email and account details.
- Enable two-factor authentication (2FA) on your email account and other critical services tied to your Flickr login.
4. Watch for warning signs
Over the next few weeks, watch for:
- Emails from look-alike domains (e.g. flickr-support[.]com)
- Messages referencing your real Flickr activity to gain trust
- Unexpected changes to your Flickr profile or settings
What we know about the investigation
- Flickr says access to the affected system has been fully disabled.
- Impacted users are being notified directly via email.
- Additional safeguards and third-party monitoring controls are being implemented.
As of now, there are no confirmed reports of a public data dump tied to this incident on major breach forums or monitoring services. That could change as investigations continue.
Frequently Asked Questions (FAQ)
Was Flickr hacked directly?
No. Flickr says the issue originated with a third-party email service provider, not Flickr’s own infrastructure.
Were passwords or credit cards leaked?
No. Flickr states passwords and payment data were not exposed.
Should I delete my Flickr account?
There is no indication this is necessary. Improving email and password hygiene is a more effective response.
Is this incident fully resolved?
The affected system has been shut down, but the investigation is still ongoing.
Final Thoughts
This incident highlights a growing reality of modern cybersecurity: even secure platforms can be affected by third-party supply-chain weaknesses.
While there is no evidence (yet) of mass exploitation, Flickr users should treat this as a serious warning and take basic protective steps now especially against phishing.
Staying cautious today can prevent account takeovers and identity misuse tomorrow.
📲 Join our WhatsApp channel for real-time breach and scam alerts
🔗 Follow us on LinkedIn for ongoing cybersecurity updates and analysis

