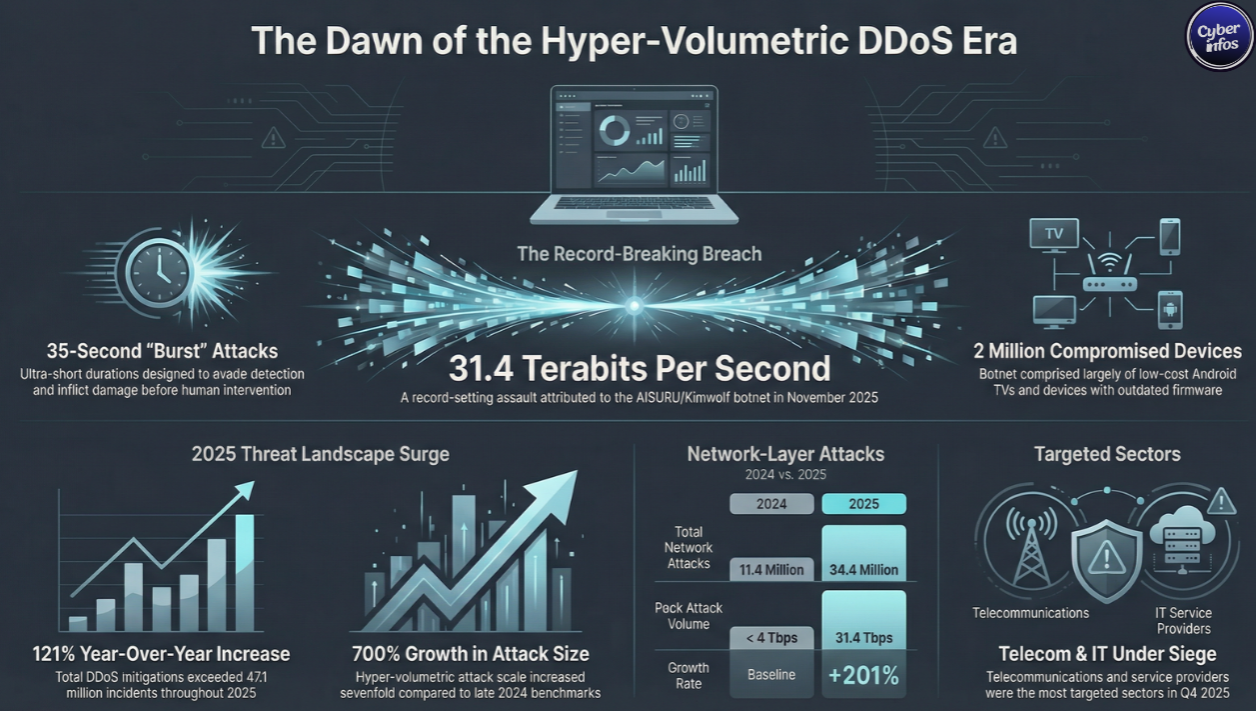
A newly attributed record-breaking distributed denial-of-service (DDoS) attack has underscored just how extreme modern cyberattacks have become. The AISURU/Kimwolf botnet is now believed to be behind a 31.4 (Tbps) terabits-per-second assault that lasted just 35 seconds, making it one of the most powerful DDoS attacks ever observed.
The attack occurred in November 2025 and was automatically detected and mitigated by Cloudflare, preventing disruption despite its unprecedented scale. According to Cloudflare, this incident was part of a broader surge in hyper-volumetric HTTP DDoS attacks throughout Q4 2025, a trend that shows no signs of slowing.
What Happened and Why It Matters
DDoS attacks overwhelm websites or online services by flooding them with massive volumes of malicious traffic. While large attacks are nothing new, 31.4 Tbps pushes well beyond what most organizations—even large ones—can withstand without cloud-based mitigation.
What makes this incident especially alarming is not just its size, but its efficiency. Lasting only seconds, the attack was likely designed to test detection thresholds, evade traditional defenses, or inflict damage before human response teams could react.
Cloudflare says this reflects a new reality: short-lived but ultra-powerful attacks that rely on automation, scale, and compromised consumer devices.
Inside the AISURU/Kimwolf Botnet
AISURU/Kimwolf is a massive botnet made up of more than 2 million Android devices, most of them:
- Off-brand or low-cost Android smart TVs
- Devices running outdated firmware
- Systems compromised without user awareness
These infected devices are frequently routed through residential proxy networks, allowing attackers to disguise malicious traffic as legitimate home-user activity.
One such network, IPIDEA, played a key role in enabling the botnet’s operations.
The “Night Before Christmas” DDoS Campaign
Cloudflare has also linked AISURU/Kimwolf to a separate DDoS campaign dubbed “The Night Before Christmas,” which began on December 19, 2025.
During this campaign, Cloudflare observed sustained hyper-volumetric attacks with staggering averages:
- 3 billion packets per second (Bpps)
- 4 Tbps
- 54 million requests per second (Mrps)
At peak intensity, attacks reached:
- 9 Bpps
- 24 Tbps
- 205 Mrps
These figures highlight how attackers are no longer relying on single, prolonged attacks, but instead launching waves of massive, precisely timed bursts.
DDoS Attacks Exploded in 2025
According to Cloudflare researchers Omer Yoachimik and Jorge Pacheco, the overall DDoS landscape deteriorated rapidly in 2025:
- DDoS attacks surged by 121% year-over-year
- An average of 5,376 attacks were mitigated every hour
- Total attacks exceeded 47.1 million, more than double 2024’s total
At the network layer alone, Cloudflare mitigated:
- 34.4 million attacks in 2025
- Compared to 11.4 million in 2024
In Q4 2025, network-layer attacks accounted for 78% of all DDoS activity, with total attacks rising 31% quarter-over-quarter and 58% year-over-year.
Hyper-Volumetric Attacks Are Getting Bigger — Fast
Not only are attacks becoming more frequent, they are becoming dramatically larger:
- Hyper-volumetric attacks increased 40% from Q3 to Q4 2025
- Attack counts rose from 1,304 to 1,824
- Attack size grew by over 700% compared to late 2024
For organizations relying on legacy, on-premise DDoS appliances, these numbers are deeply concerning.
Google and Cloudflare Disrupt IPIDEA
In a coordinated response, Google recently disrupted IPIDEA’s infrastructure, taking legal action to shut down dozens of domains used to control infected devices and proxy traffic.
Cloudflare partnered in this effort by:
- Suspending abusive accounts
- Disrupting DNS resolution for IPIDEA-controlled domains
- Blocking infrastructure used for malware distribution and proxy services
“Threat actors were attempting to distribute malware and provide markets for people seeking access to the network of illicit residential proxies,” Cloudflare told The Hacker News.
How IPIDEA Enrolled Millions of Devices
Investigations suggest IPIDEA enrolled devices through:
- 600+ trojanized Android apps embedding proxy SDKs
- 3,000+ malicious Windows binaries disguised as updates or OneDriveSync tools
- VPN and proxy apps that silently turned Android devices into proxy exit nodes
Worse still, operators are believed to run over a dozen residential proxy brands, all secretly tied to a centralized IPIDEA-controlled backend.
Who Was Targeted in Q4 2025?
Most attacked sectors
- Telecommunications
- Service providers and carriers
- Information technology
- Gambling and gaming
- Computer software
Most attacked countries
- China
- Hong Kong
- Germany
- Brazil
- United States
- United Kingdom
- Vietnam
- Azerbaijan
- India
- Singapore
Top sources of attack traffic
- Bangladesh (now the largest source)
- Ecuador
- Indonesia
- Argentina
- Hong Kong
- Ukraine
- Vietnam
- Taiwan
- Singapore
- Peru
How to Protect Your Organization from Modern DDoS Attacks
Immediate actions
- Use always-on, cloud-based DDoS protection
- Avoid relying solely on on-premise mitigation appliances
- Enable automated detection and response
- Monitor traffic baselines continuously
For consumers
- Avoid installing unofficial Android TV apps
- Keep firmware updated
- Be wary of “free” VPN or proxy apps
- Replace unsupported smart devices
Frequently Asked Questions (FAQ)
What is a hyper-volumetric DDoS attack?
An attack that overwhelms networks with extremely high traffic volumes—often measured in terabits per second or billions of packets per second.
Why are Android TVs frequently compromised?
Many run outdated software, lack security updates, and are rarely monitored by users.
Can short DDoS attacks still cause damage?
Yes. Even seconds-long attacks can disrupt services, trigger outages, or bypass slower defenses.
Final Thoughts
As Cloudflare warns, “DDoS attacks are rapidly growing in sophistication and size, surpassing what was previously imaginable.” The AISURU/Kimwolf botnet shows that attackers now have access to scale once reserved for nation-states.
For organizations still depending on legacy mitigation strategies, re-evaluating defenses is no longer optional it’s urgent.
👉 Join our WhatsApp channel for real-time cyberattack alerts
👉 Follow us on LinkedIn for weekly security insights and analysis

