When news breaks about another massive data exposure, it is easy to feel numb. Numbers blur together, headlines repeat, and it can start to feel abstract. But the recent discovery of 149 million passwords exposed online is different, because behind every one of those records is a real person, a real account, and real potential harm. This unsecured database was uncovered by respected cybersecurity researcher Jeremiah Fowler, and it offers a stark look at how modern cybercrime quietly reaches into everyday digital life.
The findings were responsibly shared with ExpressVPN, which published the report to inform and protect the public. What makes this incident especially unsettling is not just the size of the leak, but how immediately usable the stolen login credentials exposed actually were. This was not outdated or partial data—it was live access to accounts people still rely on.
What Was Sitting Open on the Internet
The database was hosted on a cloud server with virtually no security in place. There was no password required, no encryption, and no restriction on access. Anyone who happened to find the server could explore its contents using nothing more than a web browser.
Inside were 149,404,754 unique records, adding up to nearly 96 GB of raw credential data. Each record typically contained an email address or username, a plaintext password, and the exact login URL for the service. In practical terms, this meant an attacker did not have to guess anything. The door was already unlocked, and the address was written on it.
The discovery of 149 million passwords exposed shows how devastating cloud database misconfiguration breaches can be when they intersect with large-scale malware operations.
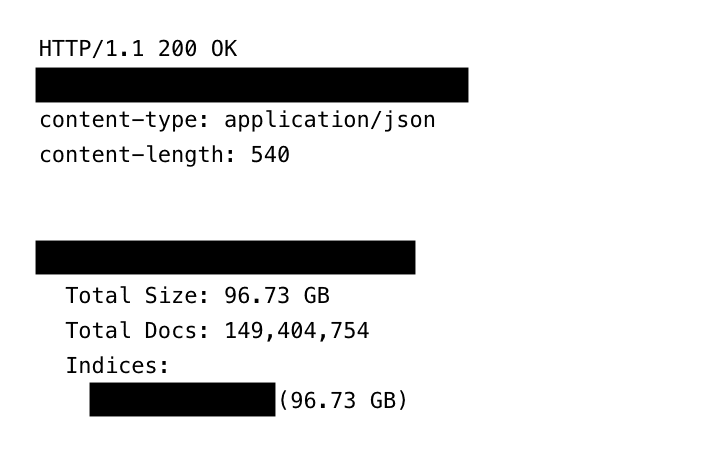
(Credit: ExpressVPN/Jeremiah Fowler)
Everyday Accounts, Not Just High-Value Targets
A closer look at even a small portion of the data made one thing clear: this exposure affected ordinary users just as much as high-profile targets. The stolen credentials covered a wide range of services people use every day, including:
- Social media platforms such as Facebook, Instagram, TikTok, and X
- Streaming and entertainment services like Netflix, Disney+, and HBO Max
- Gaming platforms including Roblox
- Dating sites and adult platforms, including OnlyFans
- Financial services such as online banking portals, credit cards, crypto wallets, and trading accounts
This massive credential breach 2026 scenario highlights an uncomfortable truth. Infostealer malware does not care who you are. Once it infects a device, it quietly gathers everything it can, from casual entertainment logins to deeply sensitive financial account credentials compromised.
Why Government and Financial Credentials Raise Alarm Bells
Among the most concerning discoveries was the presence of credentials tied to .gov email domains from multiple countries. Even if these accounts do not grant access to classified systems, exposed government email credentials can still be extremely valuable to attackers.
Such accounts can be used for impersonation, targeted spear-phishing, or quietly gathering information that leads to more serious intrusions later. When those records sit alongside banking and crypto credentials, the potential damage multiplies.
With 149 million passwords exposed, cybercriminals gain the ability to run automated credential stuffing attacks at enormous scale. That means testing stolen credentials across countless services until something works. The result is a much higher risk of fraud, identity theft, and account takeover cybercrime that often blindsides victims.
How Infostealer Malware Did Its Job
The structure of the database strongly points to keylogger malware credentials and advanced infostealer tools as the source of the data. These types of malware usually spread through phishing emails, malicious attachments, fake software updates, compromised browser extensions, or misleading advertisements.
What stood out in this case was how carefully the data was organized. The records used reversed host paths and unique line-hash identifiers, making the dataset easy to search and manage without duplicates. This shows how infostealer malware data leaks have evolved. They are no longer messy collections of stolen files, but well-structured systems designed for efficiency and scale.
A Slow Takedown That Increased the Damage
The exposed server offered no clear information about who owned or managed it. Following responsible disclosure practices, Fowler reported the issue to the hosting provider through official abuse-reporting channels. Unfortunately, the response was slow and complicated.
Responsibility appeared to shift between different entities, including a subsidiary operating under the same parent organization. It took nearly a month, along with repeated follow-ups, before the database was finally restricted.
Even more troubling, the number of records continued to grow during this period. That means additional stolen login credentials exposed were being added while the data remained publicly accessible, further increasing the identity theft risk from data leaks.
Why This Exposure Hits So Hard
The real danger of 149 million passwords exposed lies in how complete the data was. Many breaches involve hashed passwords or partial information, which slows attackers down. This dataset removed those barriers entirely.
- Launch large-scale credential stuffing attacks
- Take over email, banking, and social media accounts
- Create phishing messages that feel disturbingly real
- Build detailed digital profiles of individuals
Once an email account is compromised, the fallout often spreads quickly. Password reset links, personal documents, private conversations, and even work-related communications can all be pulled into the same compromise. For many people, the damage does not appear immediately, but unfolds over time.
Practical Steps to Reduce Your Risk
If malware is present on a device, changing passwords alone will not solve the problem. Any new credentials can be captured just as easily.
The first step is securing the device itself. This means updating the operating system, installing reputable antivirus software, and reviewing programs, browser extensions, and mobile app permissions for anything unfamiliar.
Using a password manager can help reduce harm from password reuse and basic keylogging, though it is not a complete shield against advanced malware. When combined with antivirus protection, regular updates, and strong authentication, it is still far safer than managing passwords manually.
Enabling multi-factor authentication wherever possible adds another critical barrier, even if passwords are compromised.
Final Thoughts
The story of 149 million passwords exposed online is not just about cybercriminal mistakes or technical misconfigurations. It is about how deeply digital life is woven into everyday routines, and how quietly that trust can be broken.
Infostealer malware, unsecured cloud infrastructure, and slow response processes continue to create opportunities for large-scale abuse. As attackers become more efficient, users and organizations must become more intentional. Strong authentication, antivirus protection, unique passwords, and regular account checks are no longer advanced security measures they are basic necessities. Without them, incidents involving stolen credentials exposed at massive scale will remain an unavoidable part of life online.

